
K7 total security key 2016 Archives

k7 total security key 2016 Archives
VB100 Comparative Review on Windows 8.1 Pro, 64-bit, with update
John Hawes
Virus Bulletin
Copyright © 2016 Virus Bulletin
Introduction
The platform selected for this month's comparative is Microsoft's Windows 8.1. When first released with the standard hype and fanfare it seemed like another fairly major step in the gradual expansion and improvement of the world's most popular platform, but in hindsight it joins Windows Vista as another temporary stopgap, killing time between two much more popular and successful versions of Windows. With the huge efforts being put into encouraging, cajoling and even tricking users into upgrading to Windows 10, and the bulk of the hold-outs being confirmed Windows 7 users, there seems little chance that we will be running another test on this platform. In itself, it's not a bad operating system, but in comparison with those either side, it has clearly failed to grab the attention and affection of users, and so is condemned to a slow and undignified death.
For those still tied to it for one reason or another, of course, it remains crucial to maintain a decent level of protection from malware. Therefore, we plough through the products available one more time to provide guidance for those in need.
Platform and test sets
Setting up Windows 8.1 is a fairly clean and easy process, although anyone wanting to build multiple matching machines may be mystified by its rather random approach to disk partitioning. For the purposes of this test we had to do little more than revive some images created for earlier comparatives, and update them with the latest testing tools and scripts. As usual, updates were kept to a minimum, and the bulk of the set‑up work went into preparing the sample sets.
Our main certification sets included the latest WildList available on the deadline day – the February 2016 list, released on the test deadline, 17 February. Our other test sets were given their usual clean-and-tidy routine, with the clean sets included in the certification process also frozen on the test deadline; they came to 775,000 files, 168GB.
Other sets were built according to our standard protocols, with performance test sets given no more than minor tweaks to keep the tests running as smoothly and repeatably as possible. With everything in place, we got down to working through the long list of participating products.
Business products
Avira Pro
Main version: 2016, update 16
Update versions: 8.12.70.228, 8.12.74.126, 8.12.76.138
Last 6 tests: 4 passed, 0 failed, 2 no entry
Last 12 tests: 9 passed, 0 failed, 3 no entry
ItW on demand: 100.00%
ItW on access: 100.00%
False positives: 0
Stability: Solid
 | 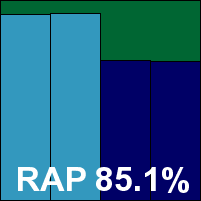 |
Getting us under way this month is Avira's premium solution, which has a pretty strong record in our tests and generally does well. Once again stability was very strong indeed, with no problems even under heavy pressure. Detection was also pretty good and performance impact was light. The core certification sets presented no difficulties, and the first VB100 award of the month is neatly claimed by Avira.
ESTsoft ALYac
Main version: 3.0.0.5
Update versions: 15.10.21.1/574606.2016021701/7.64530/6108993.20160217, 15.10.21.1/586674.2016041816/7.65196/6386339.20160418
Last 6 tests: 5 passed, 0 failed, 1 no entry
Last 12 tests: 10 passed, 0 failed, 2 no entry
ItW on demand: 100.00%
ItW on access: 100.00%
False positives: 0
Stability: Fair
 | 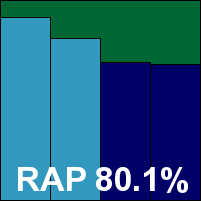 |
Bitdefender-based ESTsoft has built up a healthy list of passes over the last few years, and put in a reasonable showing once again this month. However, due to some issues with the product's logging system, which seemed to collapse if required to record more than a handful of events, our additional detection figures proved somewhat unreliable, with the bulk of the usable data coming from a single usable run. Fortunately, the certification sets presented far fewer problems and were completed successfully, so we are able to record a VB100 pass for ESTsoft this month.
Fortinet FortiClient
Main version: 5.0.9.1349
Update versions: 5.220/32.676, 33.099, 33.263, 33.423
Last 6 tests: 5 passed, 0 failed, 1 no entry
Last 12 tests: 9 passed, 1 failed, 2 no entry
ItW on demand: 100.00%
ItW on access: 100.00%
False positives: 0
Stability: Solid
 | 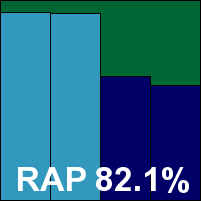 |
Fortinet's business client solution has a solid record in our tests, and put in another good showing this month with no stability problems, decent detection rates, a noticeable but not overly intrusive impact on the system speed, and no problems in the certification sets, comfortably earning the product another VB100 award.
Hammock AssetView
Main version: 8.1.5.1004
Update versions: 8.3.4.4
Last 6 tests: 1 passed, 0 failed, 5 no entry
Last 12 tests: 1 passed, 0 failed, 11 no entry
ItW on demand: 100.00%
ItW on access: 100.00%
False positives: 0
Stability: Solid
 | 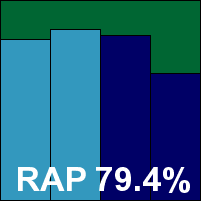 |
A newcomer to our tests this month, Hammock hails from Japan and provides a comprehensive business solution; the bulk of the malware-detection is provided by the Kaspersky engine. The product proved rather more complex to set up and operate than we are used to, but with some assistance from the developers we eventually got it running, and saw no stability issues, decent detection, acceptable performance impact and a good showing in our certification sets. Hammock's first VB100 award is well deserved.
Ikarus anti.virus
Main version: 2.9.26
Update versions: 96169, 96601, 97058, 97627
Last 6 tests: 3 passed, 1 failed, 2 no entry
Last 12 tests: 8 passed, 1 failed, 3 no entry
ItW on demand: 100.00%
ItW on access: 100.00%
False positives: 16
Stability: Fair
 | 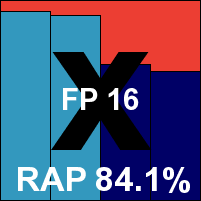 |
Ikarus has been maintaining a good run of VB100 passes in the last few years, but this month returned to old habits, sprinkling false alarms through our clean sets. These included a handful of alerts about a DDoS trojan in a popular Linux tool and some issues with a CAD solution. Otherwise things went pretty well, stability was mostly OK although we did note a few crashes, mostly when not doing anything particularly stressful. The WildList set was well covered, but with that rash of false positives in the clean set no VB100 award is granted this month.
iSheriff Security from the Cloud
Main version: 5.8.0
Update versions: 5.8.0.0215/3.71, 5.8.1/5.8.1.0000
Last 6 tests: 3 passed, 2 failed, 1 no entry
Last 12 tests: 8 passed, 2 failed, 2 no entry
ItW on demand: 100.00%
ItW on access: 100.00%
False positives: 161
Stability: Fair
 |  |
Another very regular product, and another which has recently had some problems with false positives. The Bitdefender engine, present in almost half of the products being tested this month, is integrated into the iSheriff product alongside the company's own technologies; it is a complete business product operated from a cloud portal. Stability was mostly fine, apart from a single incident during the performance tests where the product claimed the Internet was down and couldn't communicate with its control systems, rendering it unusable. The WildList sets were handled well, but once again we saw a barrage of false alarms, mainly on DLL files from major software houses including Dell and SAP, which means there is no VB100 award for iSheriff this month, despite a generally good showing.
Microsoft System Center Endpoint Protection
Main version: 4.9.218.0
Update versions: 1.1.12400.0/1.213.6009.0, 1.1.12505.0/1.215.565.0, 1.215.1582.0, 1.215.2503.0
Last 6 tests: 4 passed, 0 failed, 2 no entry
Last 12 tests: 9 passed, 0 failed, 3 no entry
ItW on demand: 100.00%
ItW on access: 100.00%
False positives: 0
Stability: Solid
 | 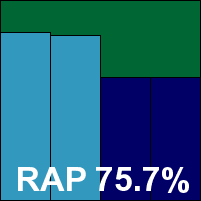 |
Microsoft's business offering is essentially a set of management tools connected to the Defender solution, at the desktop level at least. It generally puts in a good performance, and this occasion was no different, with rock-like stability through the tests and decent detection rates across the board. Performance measures were mostly very close to our baselines taken with standard Defender active, although our set of activities was a little slower. With a clean run through the certification sets, another VB100 award goes to Microsoft.
MSecure DenyWall Antivirus
Main version: 1.1.107.0
Update versions: 96169, 96599, 97075, 97627
Stability rating: Fair
Last 6 tests: 0 passed, 1 failed, 5 no entry
Last 12 tests: 0 passed, 3 failed, 9 no entry
ItW on demand: 100.00%
ItW on access: 2.75%
False positives: 47
Stability: Fair
 |  |
MSecure's products have appeared in a number of our tests in recent years, but haven't managed to achieve a pass in some time, mainly thanks to a rather glaring issue which meant the content of the extension list was largely ignored, meaning several of the most common malicious file types were not scanned by default on access. There were some other issues to note this month, including an unexpected restart and some logging inconsistencies, but the lingering detection problem was the most serious. Despite decent detection on demand, scores were very low indeed on access, and a glut of false positives in the clean sets confirms that there is no VB100 award for MSecure this time. A new and completely reworked product is promised for the near future, which should hopefully fare better.
Quick Heal Seqrite Endpoint Security
Main version: 16.00
Update versions: 9.0.32.1 64Bit
Last 6 tests: 4 passed, 0 failed, 2 no entry
Last 12 tests: 5 passed, 0 failed, 7 no entry
ItW on demand: 100.00%
ItW on access: 100.00%
False positives: 0
Stability: Solid

Quick Heal's business product line has only been appearing in our tests for the last couple of years, but has a good string of passes accumulating already. Performance hit was not the lowest but not excessive, and detection was decent in the response tests. Some problems with the submission meant we could not gather a full set of RAP data, but other tests ran without problems and a VB100 award is well deserved.
TrustPort Antivirus 2015
Main version: 2015(15.0.5.5440)
Update versions: N/A
Last 6 tests: 4 passed, 0 failed, 2 no entry
Last 12 tests: 6 passed, 0 failed, 6 no entry
ItW on demand: 100.00%
ItW on access: 100.00%
False positives: 0
Stability: Stable
 | 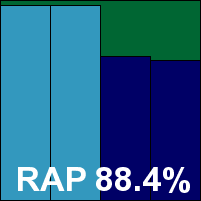 |
Dual-engine TrustPort can usually be relied upon for some impressively high detection rates. This month, the product is included in the business category despite, according to its creators, being suitable for both home and office use. The only stability problem observed was an issue with the update button, which decided to stop functioning from time to time, but otherwise all was steady. Performance impact was impressively light for a product with such excellent coverage of malware, and with no problems in the clean sets a VB100 award is easily earned.
Consumer Products
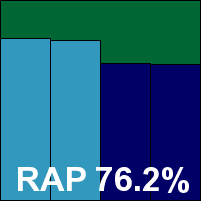
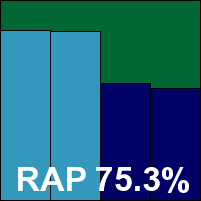
ALLIT Service Zillya! Internet Security
Main version: 2.0.4785.0
Update versions: 2.0.0.2261, 2.0.0.2708, 2.0.0.2725, 2.0.0.2737
Last 6 tests: 0 passed, 2 failed, 4 no entry
Last 12 tests: 0 passed, 2 failed, 10 no entry
ItW on demand: 76.17%
ItW on access: 75.03%
False positives: 48
Stability: Fair
 |  |
We've seen Zillya! a few times before in our tests, with the standard required for VB100 certification not yet reached. This month it had a few, mostly fairly minor stability problems, mainly GUI freezes and crashes while scanning, and detection was fairly mediocre with low scores in our sets of recent samples. Quite a few WildList items went undetected, and we noted a fair number of false alarms in our clean sets, including classing a part of the Firefox browser as a worm. Thus no VB100 award is granted to ALLIT Service this month, although we are seeing steady improvement in the product.
Avast Free Antivirus
Main version: 11.1.2253
Update versions: 160216-0, 160307-0, 160314-0, 160321-0
Last 6 tests: 6 passed, 0 failed, 0 no entry
Last 12 tests: 11 passed, 1 failed, 0 no entry
ItW on demand: 100.00%
ItW on access: 100.00%
False positives: 0
Stability: Solid
 | 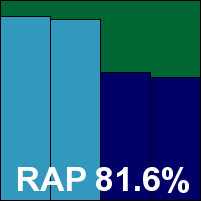 |
A regular strong performer, Avast's free edition put in another good showing with solid stability and strong detection levels. The only dent in this month's performance was a rather high impact on our set of activities, which took several times longer than the baseline, rather unusually for this product which has performed the same test pretty rapidly in the past. A clean run through our certification sets comfortably earns Avast another VB100 award.
AVG AntiVirus
Main version: 16.41.7442
Update versions: 4530/11630, 4540/11769, 11813, 4542/11858
Last 6 tests: 6 passed, 0 failed, 0 no entry
Last 12 tests: 12 passed, 0 failed, 0 no entry
ItW on demand: 100.00%
ItW on access: 100.00%
False positives: 0
Stability: Solid
 | 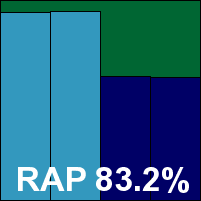 |
AVG can proudly boast of being one of the few products with a clean sheet of passes in the last dozen tests. The product's performance this month was strong once again, with flawless stability under pressure, good detection rates and only a fairly heavy impact on our set of tasks to complain about. A VB100 award is well deserved, adding to that pleasingly unbroken chain of passes.
Avira Free Antivirus
Main version: 2016, update 16
Update versions: 8.12.70.228, 8.12.74.126, 8.12.76.138
Last 6 tests: 2 passed, 0 failed, 4 no entry
Last 12 tests: 5 passed, 0 failed, 7 no entry
ItW on demand: 100.00%
ItW on access: 100.00%
False positives: 0
Stability: Solid
 | 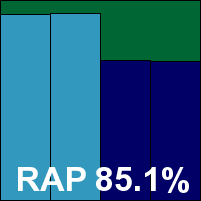 |
Avira's free edition tends to only show up in our desktop tests, generally putting in the same sort of splendid performances as we see more regularly from the vendor's premium and corporate editions. This month was much the same, with pretty light performance hit, decent detection and a clean run through the main sets, earning Avira another VB100 award.
Bitdefender Antivirus Plus 2016
Main version: 20.0.25.1378
Update versions: 7.64536/6106005, 7.64780/5857537, 7.64852/5895401, 7.64913/6088530
Last 6 tests: 6 passed, 0 failed, 0 no entry
Last 12 tests: 12 passed, 0 failed, 0 no entry
ItW on demand: 100.00%
ItW on access: 100.00%
False positives: 0
Stability: Solid
 | 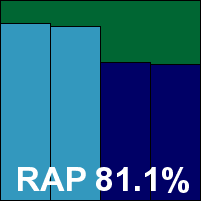 |
Bitdefender can also show off with an unbroken string of passes in all of our tests over the last two years, with the company's engine also playing a key part in many other successful products. This month there were no upsets, with another excellent showing across the board, although detection numbers were a shade lower than we're used to. The core sets were handled impeccably once again, and another VB100 award is well deserved.
BullGuard Antivirus
Main version: 16.0.314.5
Update versions: 7.64537, 16.0.316.1/7.64780, 16.0.316.1/7.64853, 16.0.317.1/ 7.64913
Last 6 tests: 3 passed, 0 failed, 3 no entry
Last 12 tests: 7 passed, 0 failed, 5 no entry
ItW on demand: 100.00%
ItW on access: 100.00%
False positives: 0
Stability: Solid
 | 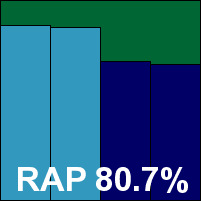 |
BullGuard is one of the long list of products integrating Bitdefender's engine, something the firm has been doing very well for quite some time. It was another good job this month, with dependably good detection rates and minimal performance hit. The certification sets were nicely managed, earning BullGuard another VB100 award.
Check Point Zone Alarm Extreme Security
Main version: 14.1.048.000
Update versions: 8.6.0.97
Last 6 tests: 2 passed, 0 failed, 4 no entry
Last 12 tests: 5 passed, 0 failed, 7 no entry
ItW on demand: 100.00%
ItW on access: 100.00%
False positives: 0
Stability: Stable
 | 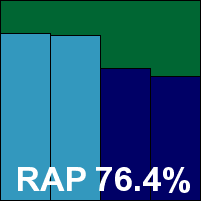 |
Bucking the trend somewhat, Check Point bundles the Kaspersky engine alongside its own technology as part of the venerable Zone Alarm product line. It did well once again this month, with decent detection, although our set of tasks was a little slower than the baseline. The certification sets were properly dealt with, and a VB100 award is merited.
CompuClever Antivirus Plus
Main version: 19.2.0.151
Update versions: 7.62494, 19.4.0.239/7.64779, 7.64852, 7.64913
Last 6 tests: 2 passed, 0 failed, 4 no entry
Last 12 tests: 2 passed, 0 failed, 10 no entry
ItW on demand: 100.00%
ItW on access: 100.00%
False positives: 0
Stability: Solid
 | 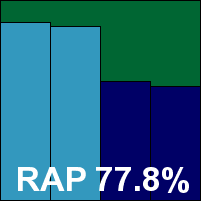 |
A somewhat newer name in our tests, CompuClever managed its first pass at the end of 2015 and is back for more. Once again using the Bitdefender engine, it put in a decent showing with low performance hit and decent scores. The RAP figures were a little lower than for some other Bitdefender users, but this is probably due to submission timing rather than anything more serious. The WildList and clean sets presented no problems, and a second VB100 award is earned by CompuClever.
CYREN Command Anti-Malware
Main version: 5.1.35
Update versions: 5.4.20
Last 6 tests: 2 passed, 3 failed, 1 no entry
Last 12 tests: 3 passed, 7 failed, 2 no entry
ItW on demand: 100.00%
ItW on access: 100.00%
False positives: 0
Stability: Stable
 | 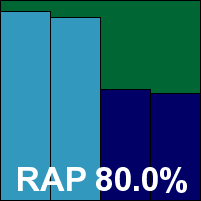 |
On the surface at least, CYREN's Command product remains one of the least changed for quite some time, with the simple and minimalist interface a very familiar sight on the VB test bench. Under the covers it has seen some serious work though, with the company's cloud look‑up system providing an impressive boost in detections over the last few years. This has often come at the expense of a higher false alarm rate, but this month there were no such problems; superb detection was recorded in the response sets, with the offline part of the RAP tests clearly demonstrating the importance of the cloud look‑ups. As usual, our set of tasks was fairly heavily slowed down, but a clean run through the certification sets earns CYREN another VB100 award.
Emsisoft Anti-Malware
Main version: 11.0.0.6131
Update versions: 3.5.0.656/11.0.1.12, 11.5.0.6191, 11.5.0.6191, 11.5.1.6247
Last 6 tests: 5 passed, 0 failed, 1 no entry
Last 12 tests: 10 passed, 0 failed, 2 no entry
ItW on demand: 100.00%
ItW on access: 100.00%
False positives: 0
Stability: Fair
 | 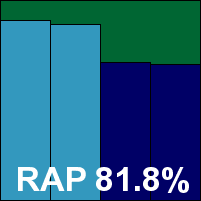 |
Emsisoft has earned VB100 passes in all of our Windows tests in recent years, with only our annual visits to Linux missed out. This month we saw decent detections along the lines of others using the same Bitdefender engine, a very light impact on system speeds and a good showing in the core sets, earning the product another VB100 award.
eScan Internet Security Suite for Windows
Main version: 14.0.1400.1860 DB
Update versions: N/A
Last 6 tests: 6 passed, 0 failed, 0 no entry
Last 12 tests: 12 passed, 0 failed, 0 no entry
ItW on demand: 100.00%
ItW on access: 100.00%
False positives: 0
Stability: Fair
 | 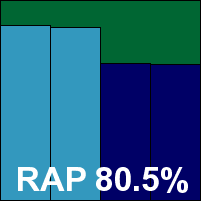 |
Another product maintaining a flawless record of passes in all tests in the last few years, the eScan suite also includes the Bitdefender engine and scored predictably well, with low resource use but a fairly notable hit on our set of activities. The certification sets were dealt with well, and that perfect record of VB100 passes is maintained.
ESET NOD32 Antivirus
Main version: 9.0.349.14
Update versions: 13042, 13139, 13174, 9.0.375.0/13212
Last 6 tests: 6 passed, 0 failed, 0 no entry
Last 12 tests: 12 passed, 0 failed, 0 no entry
ItW on demand: 100.00%
ItW on access: 100.00%
False positives: 0
Stability: Stable
 | 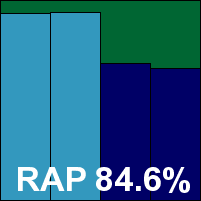 |
ESET's record in our tests speaks for itself, with an unbroken run of passes going way back into the past affirming the solid reliability of the company's products. There were a couple of very minor glitches this month, including a button offering a new version which seemed to do nothing, but otherwise all was as good as ever, with a light system footprint and strong detection, extending as usual to the certification sets which were brushed aside effortlessly to earn yet another VB100 award for ESET.
Essentware PCKeeper Antivirus PRO
Main version: 8.3.36.16
Update versions: 8.12.58.254, 8.3.36.42/8.12.66.134, 8.3.36.54/8.12.69.118, 8.3.38.0/8.12.72.206
Last 6 tests: 2 passed, 0 failed, 4 no entry
Last 12 tests: 3 passed, 0 failed, 9 no entry
ItW on demand: 100.00%
ItW on access: 100.00%
False positives: 0
Stability: Solid
 | 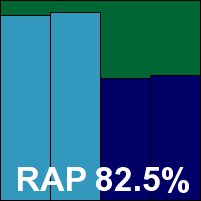 |
The PCKeeper brand has been popping up in our tests for some time under various different owners, and on this occasion returns for its second attempt under the Essentware umbrella. Bundling the Avira engine with a few additional tricks, it scored very well indeed in the response tests, dropping down a fair bit in the offline parts of the RAP tests. RAM usage was a touch high, but our set of activities was not too heavily slowed down, and a clear run through the certification sets earns the product another VB100 award.
G Data Antivirus
Main version: 25.1.0.10
Update versions: AVA 25.5548/GD 25.6.373, AVA 25.5807/GD 25.6495, AVA 25.5879/GD 25.6535, AVA 25.5943/GD 25.6565
Last 6 tests: 5 passed, 0 failed, 1 no entry
Last 12 tests: 9 passed, 0 failed, 3 no entry
ItW on demand: 100.00%
ItW on access: 100.00%
False positives: 0
Stability: Solid
 | 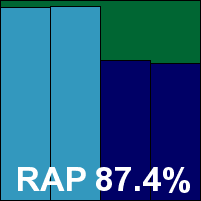 |
When G Data changed from using two third-party engines to a combination of Bitdefender and the company's own in-house technology, we predicted some dropping off in detection rates from the superb heights we were used to. However, our prediction has repeatedly been proved wrong over the course of the last few tests, as the product continues to impress with its breadth of coverage. This month's performance was very strong once again with excellent detection rates in the RAP sets and a pleasingly low system speed impact. The core sets presented no difficulties, and G Data earns a VB100 award with another excellent showing.
Inca nProtect AVS V4.0
Main version: 2016.02.17.01
Update versions: 4.0.0.10010, 2016.03.09(1), 2016.03.17(1), 2016.03.23(1)
Last 6 tests: 2 passed, 0 failed, 4 no entry
Last 12 tests: 2 passed, 0 failed, 10 no entry
ItW on demand: 100.00%
ItW on access: 100.00%
False positives: 0
Stability: Fair
 |  |
A fairly new name on our testing roster, Inca has already notched up a pass on its first attempt at VB100 certification, and returns this month for a second try. As with so many others, the product uses the Bitdefender engine, which as usual provided some dependable detection scores. Our set of tasks showed a significant slowdown, accompanied by very high use of CPU cycles, but the certification sets were nicely handled and a VB100 award is merited.
K7 Total Security
Main version: 15.1.0.288
Update versions: 9.213.18774, 15.1.0.289/9.214.18951, 9.214.19004, 9.218.19067
Last 6 tests: 5 passed, 0 failed, 1 no entry
Last 12 tests: 9 passed, 0 failed, 3 no entry
ItW on demand: 100.00%
ItW on access: 100.00%
False positives: 0
Stability: Solid
 |  |
K7's 'Total' solution has been putting in some reliably classy performances in our comparatives over the last few years, with stability rarely challenged even by our most high-pressure tests. This month we saw another solid and dependable performance, with decent detection scores, very low resource use, and a fair but not excessive hit on our set of tasks. Good work in the certification sets easily earns K7 another VB100 award.
Kaspersky Internet Security
Main version: 16.0.1.445
Update versions: 16.0.1.445, 16.0.1.445(b), 16.0.1.445
Last 6 tests: 4 passed, 0 failed, 2 no entry
Last 12 tests: 9 passed, 0 failed, 3 no entry
ItW on demand: 100.00%
ItW on access: 100.00%
False positives: 0
Stability: Stable
 |
There was just a single product from Kaspersky Lab this month, for a change. The Internet Security suite is a regular in our tests, with some good history, and this month it put in its usual strong showing. Stability was shaken only by a single incident where the interface locked up for ten minutes or so, but managed to straighten itself out without intervention. RAP data is absent once again. The core sets were cleanly dealt with, and a VB100 award is earned by Kaspersky.
Lavasoft Ad-Aware Free Antivirus +
Main version: 11.10.767.8917
Update versions: N/A
Last 6 tests: 3 passed, 0 failed, 3 no entry
Last 12 tests: 6 passed, 0 failed, 6 no entry
ItW on demand: 100.00%
ItW on access: 100.00%
False positives: 0
Stability: Solid
 | 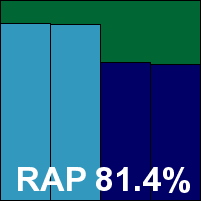 |
Lavasoft's iconic Ad‑Aware brand is represented by two versions this month, starting off with the free edition. It had no stability problems at all and scored well in our detection tests, helped by that ever-present Bitdefender engine. Performance measures were once again a bit odd, with our set of tasks held up by regular pauses waiting for some input – during this time the local system was largely idle, hence the very low average CPU usage. This does not affect certification of course, which was comfortably earned after a clean run through the certification tests.
Lavasoft Ad-Aware Pro Security
Main version: 11.10.767.8917
Update versions: N/A
Last 6 tests: 1 passed, 0 failed, 5 no entry
Last 12 tests: 1 passed, 0 failed, 11 no entry
ItW on demand: 100.00%
ItW on access: 100.00%
False positives: 0
Stability: Solid
 | 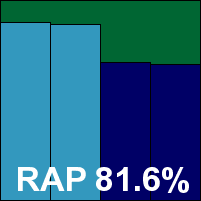 |
The 'Pro' version of Ad-Aware has a similar look and feel to the free edition, with a slight tweak to the colour scheme to differentiate the two and a few extras thrown in under the hood. It put in a similar performance, with solid stability, strong detection, some issues with our set of tasks but no problems in the certification sets, earning Lavasoft another VB100 award this month.
Maya PremiumIS
Main version: 2.0.88.147
Update versions: 2.0.88.147, 2.0.89.148, 2.0.89.148
Last 6 tests: 0 passed, 2 failed, 4 no entry
Last 12 tests: 0 passed, 4 failed, 8 no entry
ItW on demand: 21.22%
ItW on access: N/A
False positives: 1
Stability: Buggy
 |  |
Maya's products have made it into our reports on a couple of occasions so far, with several additional submissions having been discarded from other tests long before the final testing phases thanks to a number of stability problems. This month these problems raised their heads once more, with several crashes and freezes and, most significantly, no luck whatsoever in getting the on‑access component to work. On‑demand detection was rather feeble, and with no on‑access detection and a false positive in the clean sets to boot, we can only conclude that Maya still has some way to go before it reaches the required standard for VB100 certification.
NANO Antivirus Pro
Main version: 1.0.14.71740
Update versions: 0.14.24.6969, 1.0.18.72213/0.14.25.7107, 0.44.25.7145, 1.0.18.72737 Pro/0.14.25.7186
Last 6 tests: 1 passed, 1 failed, 4 no entry
Last 12 tests: 1 passed, 1 failed, 10 no entry
ItW on demand: 100.00%
ItW on access: 100.00%
False positives: 0
Stability: Stable
 | 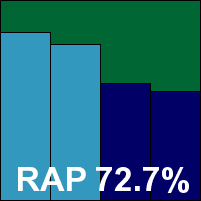 |
NANO has impressed over the last few tests with a steady trend of improvement across the board, and this month it did well once again. Stability was impeccable, system impact quite acceptable, and detection pretty decent, including flawless coverage of the WildList sets. The clean sets have been a bit of a problem in previous tests, but this month all was clear there too. Thus, just a short time after we first started looking at this all-new product, NANO should be very proud to claim its first VB100 certification.
Panda Internet Security 2016
Main version: 16.0.2
Update versions: 16.1.0
Last 6 tests: 2 passed, 0 failed, 4 no entry
Last 12 tests: 5 passed, 0 failed, 7 no entry
ItW on demand: 100.00%
ItW on access: 100.00%
False positives: 0
Stability: Fair

A fairly regular participant in our tests over the last few years, Panda has been quietly building up a decent string of passes. The heavily cloud-dependent product scored pretty well in the online parts of the RAP test, with the offline parts of the test not compatible with the product's requirements. The product showed minimal memory usage, not too much CPU usage, and our set of tasks was not too heavily delayed. The certification sets were cleanly dealt with, and another VB100 award is earned by Panda.
PC Pitstop PC Matic Home Security
Main version: 1.0.0.60
Update versions: N/A
Last 6 tests: 0 passed, 3 failed, 3 no entry
Last 12 tests: 1 passed, 5 failed, 6 no entry
ItW on demand: 88.25%
ItW on access: 62.53%
False positives: 101
Stability: Fair
 |  |
PC Pitstop's fairly unusual combination of whitelisting alongside a 'traditional' malware detection engine has proved pretty strong at flagging up malware over the last few years, balanced as one would expect with a rather higher than average rate of false positives. There were some false positives once again this month, although this still only represented 0.013% of our full clean sets, so they are likely to be fairly rare in the real world. The detection rate was strong and consistent across all sets, even without access to the Internet. Similar scores were recorded in the WildList sets, although somewhat lower than expected, which we suspect is due to an as-yet undiagnosed problem with fitting the product into our testing system – something we hope to resolve shortly, along with a handful of freezing issues we noted during testing. No VB100 certification is awarded to PC Pitstop this month.
Qihoo 360
Main version: 5.0.0.6221
Update versions: N/A
Last 6 tests: 2 passed, 0 failed, 4 no entry
Last 12 tests: 5 passed, 0 failed, 7 no entry
ItW on demand: 100.00%
ItW on access: 100.00%
False positives: 0
Stability: Solid
 | 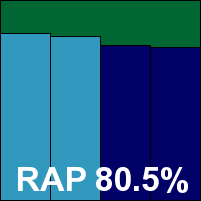 |
Qihoo's 360 brand continues to grow in stature around the world, and has a strong history in our tests of late. Its (optional) multi-engine approach has worked well, with pretty light system footprint by this month's standards. Detection rates were also good, and with no stability problems or issues in the certification sets, a VB100 award is comfortably earned.
Quick Heal Total Security
Main version: X
Update versions: 16.00/9.0.24.4 64Bit
Last 6 tests: 4 passed, 0 failed, 2 no entry
Last 12 tests: 6 passed, 0 failed, 6 no entry
ItW on demand: 100.00%
ItW on access: 100.00%
False positives: 0
Stability: Stable
 |
Our second product from Quick Heal this month has a very similar feel to its business cousin, producing similar results too. Stability was good, with only a very minor issue noted involving losing touch with our lab's Internet connection. Detection was good too, again there are no offline RAP scores thanks to issues with the submission. Performance measures showed fairly high resource usage and impact on our set of tasks, but nothing too severe. The core sets were covered nicely, and another VB100 award is earned by Quick Heal.
REVE Antivirus
Main version: 1.2.0.6
Update versions: N/A
Last 6 tests: 1 passed, 0 failed, 5 no entry
Last 12 tests: 1 passed, 0 failed, 11 no entry
ItW on demand: 100.00%
ItW on access: 100.00%
False positives: 0
Stability: Fair
 | 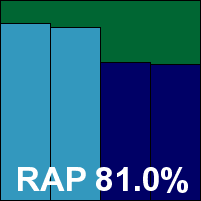 |
Another newcomer to our tests, REVE is based in India and, like many companies these days, incorporates the Bitdefender engine into its product. There were some stability issues, including updating problems, crashes during scans, and failures to start tasks properly, but for the most part things ran smoothly. Detection was strong as one would expect, and slowdown and resource usage were minimal. With the certification sets dealt with easily, a VB100 award goes to REVE for the first time.
Tencent PC Manager
Main version: 11.2.26139.901
Update versions: 11.2.26147.901, 11.2.26152.901, 11.2.26157.901
Last 6 tests: 4 passed, 0 failed, 2 no entry
Last 12 tests: 8 passed, 0 failed, 4 no entry
ItW on demand: 100.00%
ItW on access: 100.00%
False positives: 0
Stability: Solid
 | 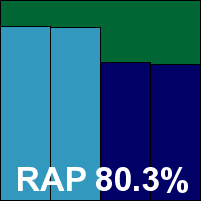 |
Tencent's PC Manager managed another very stable and reliable performance this month, with no wobbles noted and pretty reasonable impact on system speed. Detection was decent, close to that of others using the same Bitdefender engine, and the core sets presented no difficulties, earning Tencent another VB100 award.
ThreatTrack VIPRE Internet Security Pro 2016
Main version: 9.3.4.3
Update versions: 3.9.2671.2-3.0/47274/7.64536, 47750/7.64784, 47946/7.64854, 48084/7.64915
Last 6 tests: 2 passed, 0 failed, 4 no entry
Last 12 tests: 5 passed, 0 failed, 7 no entry
ItW on demand: 100.00%
ItW on access: 100.00%
False positives: 0
Stability: Stable
 | 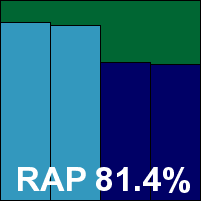 |
ThreatTrack's VIPRE was something of a revolution when it first emerged under then-owner Sunbelt Software, as one of the first completely new anti-malware engines to come to the market in many years. With the engine now retired in favour of that ever‑popular Bitdefender one, VIPRE carries on. This month's testing saw reasonable impact on the system, with the expected decent detection rates and just a single stability issue, a freeze during installation in one round of tests. The certification sets were covered properly, and a VB100 award goes to ThreatTrack.
Total Defense Internet Security
Main version: 9.0.0.422
Update versions: 3.0.2.1015/2016.2.17.9, 2016.3.9.13, 2016.3.18.7, 2016.3.23.11
Last 6 tests: 3 passed, 0 failed, 3 no entry
Last 12 tests: 5 passed, 0 failed, 7 no entry
ItW on demand: 100.00%
ItW on access: 100.00%
False positives: 0
Stability: Stable
 | 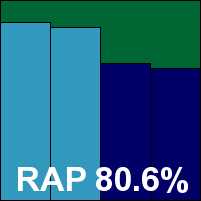 |
Total Defense is another name with a long and complicated history in our tests, and another product that is now built around the Bitdefender engine. This month we saw impressively low performance impact scores alongside the unsurprisingly decent detection levels. Stability was also decent, with just a few big scans crashing out, and a clean run over the core sets, earns Total Defense another VB100 award.
UtilTool Antivirus
Main version: 3.3.96
Update versions: 3.64.0/5.23, 5.24, 5.25, 5.25
Last 6 tests: 1 passed, 0 failed, 5 no entry
Last 12 tests: 1 passed, 0 failed, 11 no entry
ItW on demand: 100.00%
ItW on access: 100.00%
False positives: 0
Stability: Fair

The final product to cover this month will be familiar to some regular readers, having been a regular participant up until a couple of years ago. At that point it used the now-defunct VirusBuster engine, which has since been replaced by that of Sophos in an otherwise fairly similar-looking product. We saw a number of stability issues, mainly scans getting stuck, and had some trouble getting enough detection data to be usable. In the end we gave up, so no detection numbers are listed. Resource usage was fairly low, but our set of tasks was quite seriously slowed down. The certification sets mercifully did complete without problems, well enough to earn UtilTool a VB100 award on its return to the fold.
Results tables
Business products
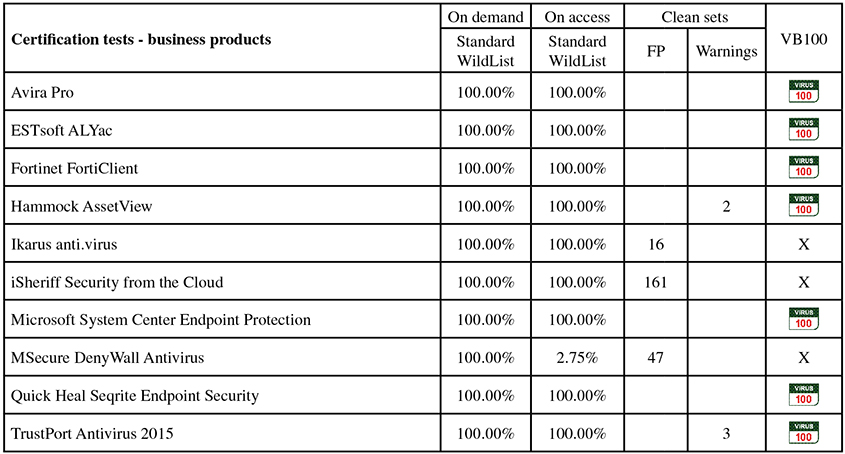
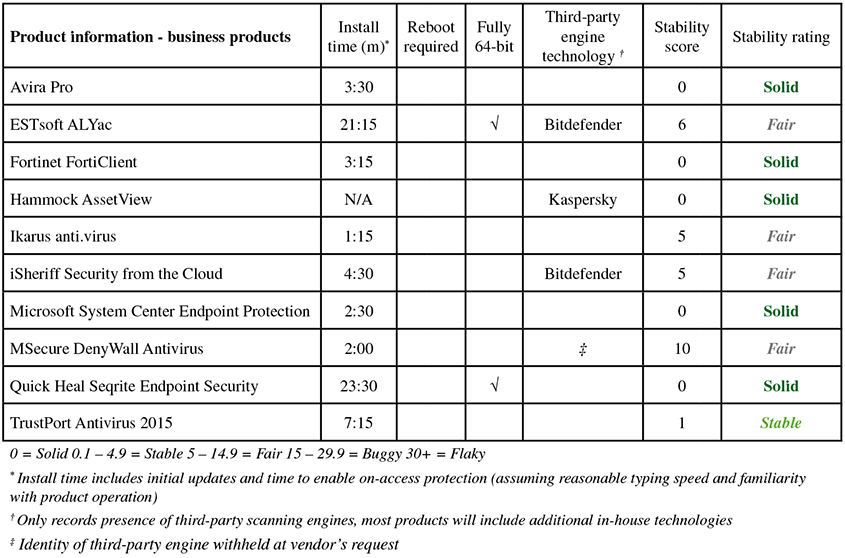
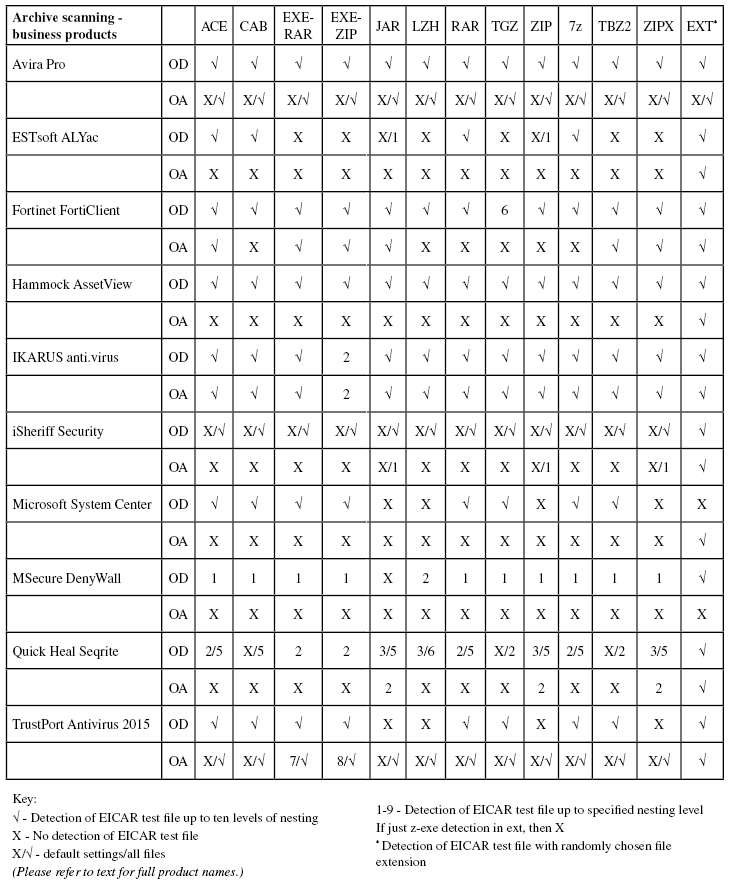
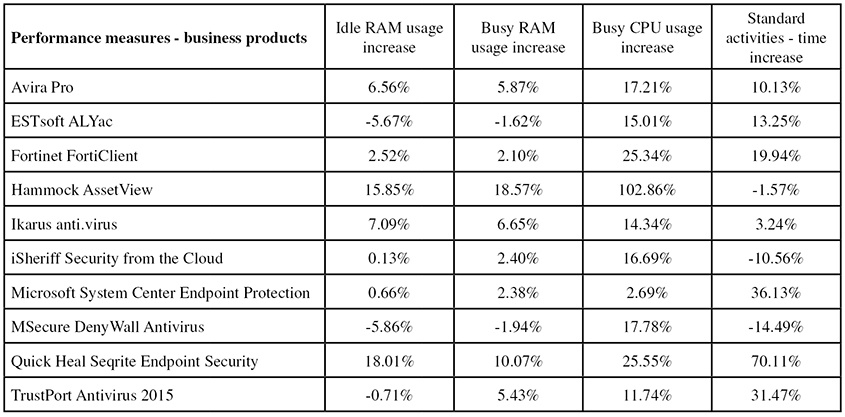
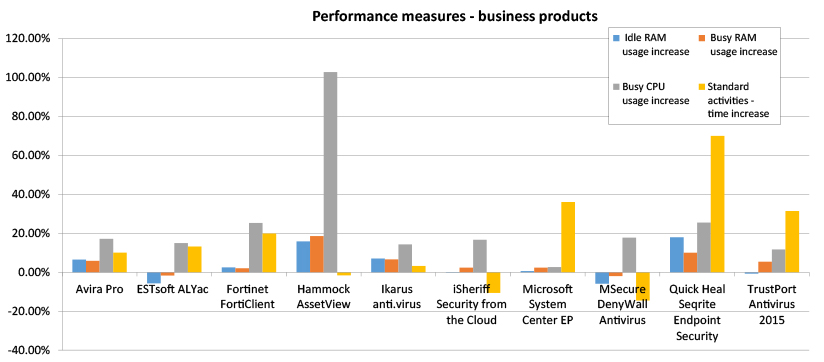
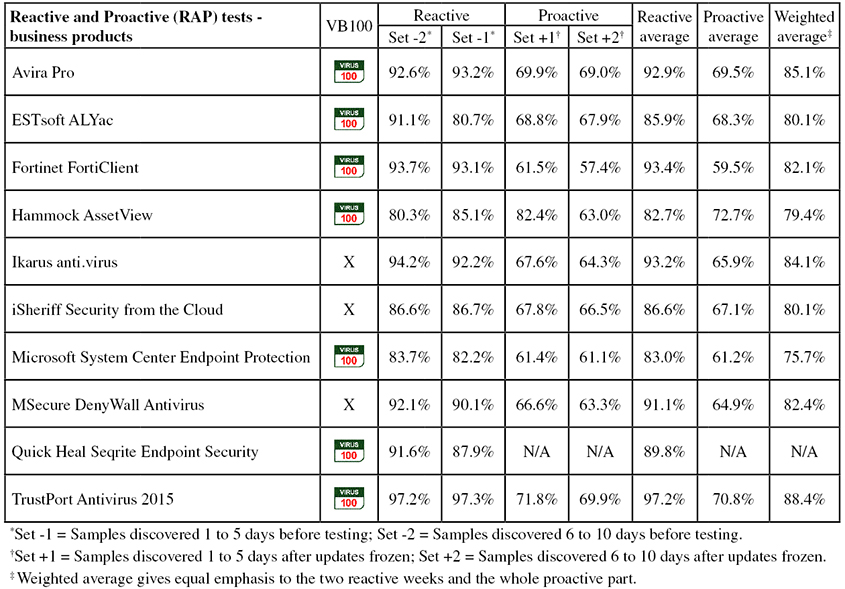
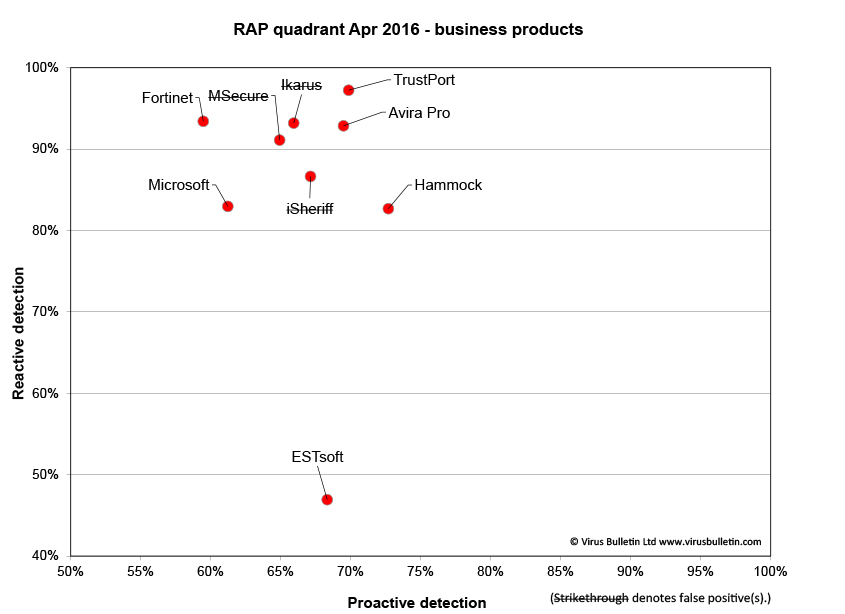
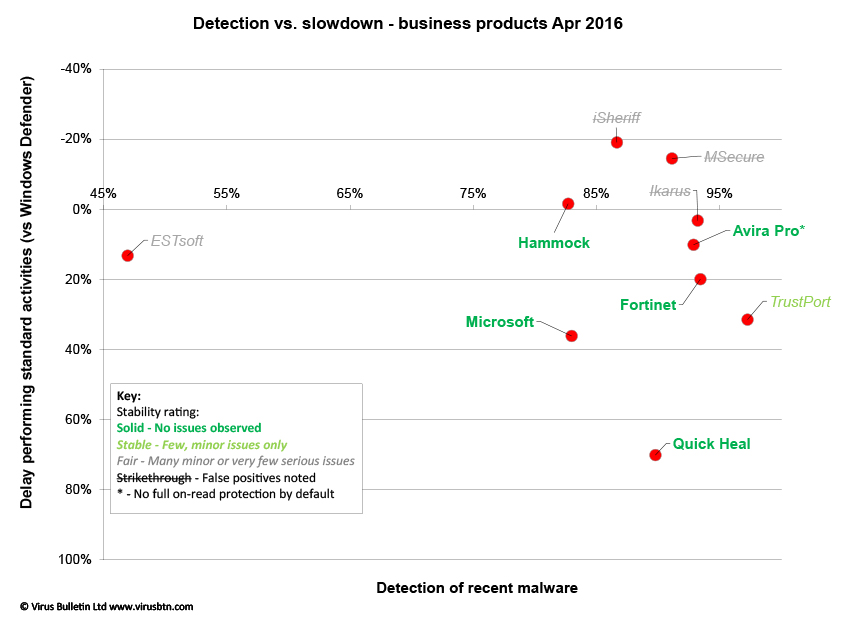
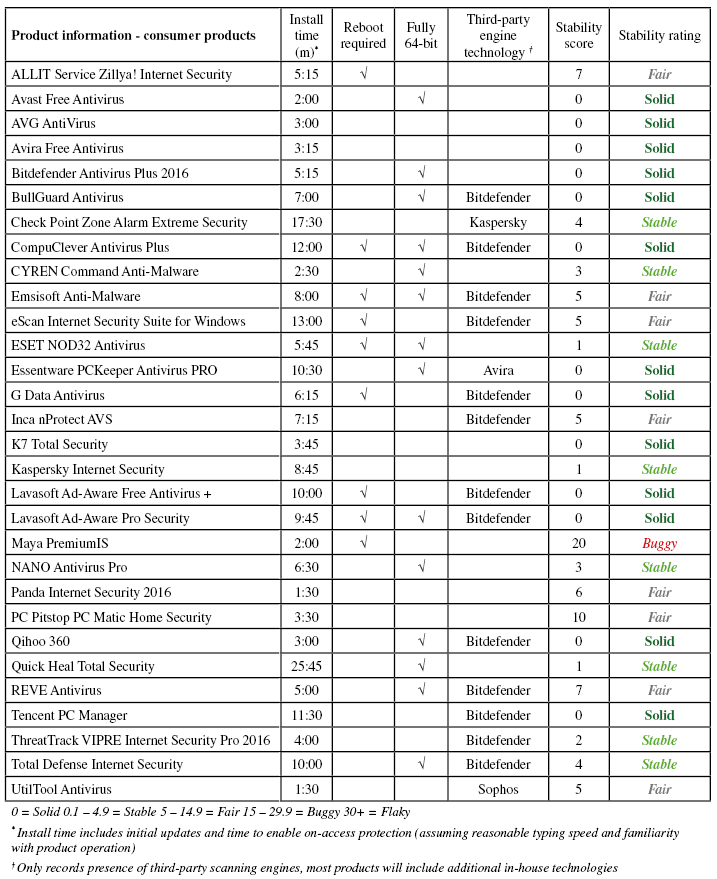
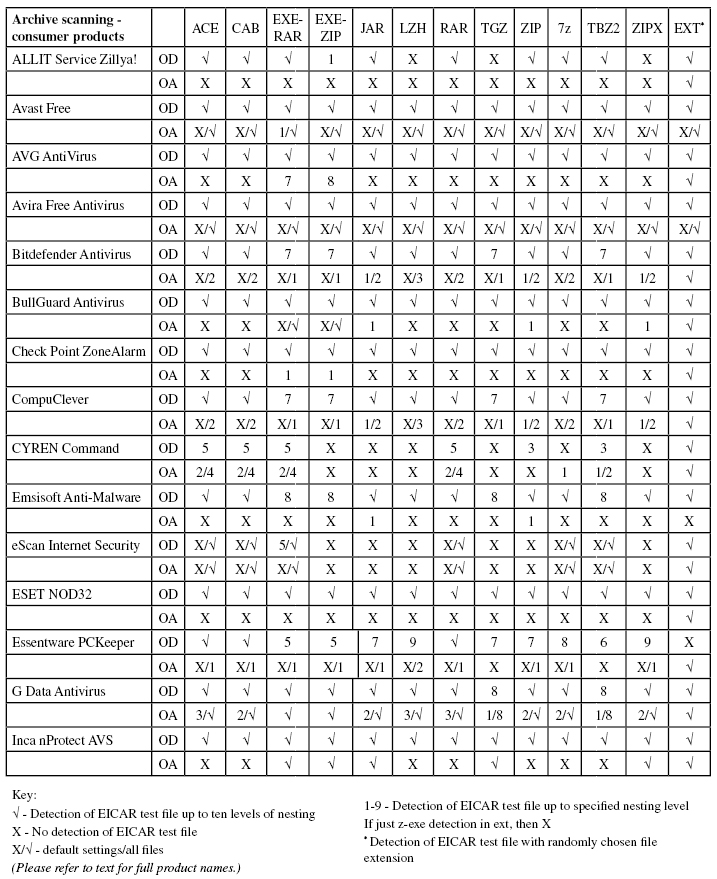
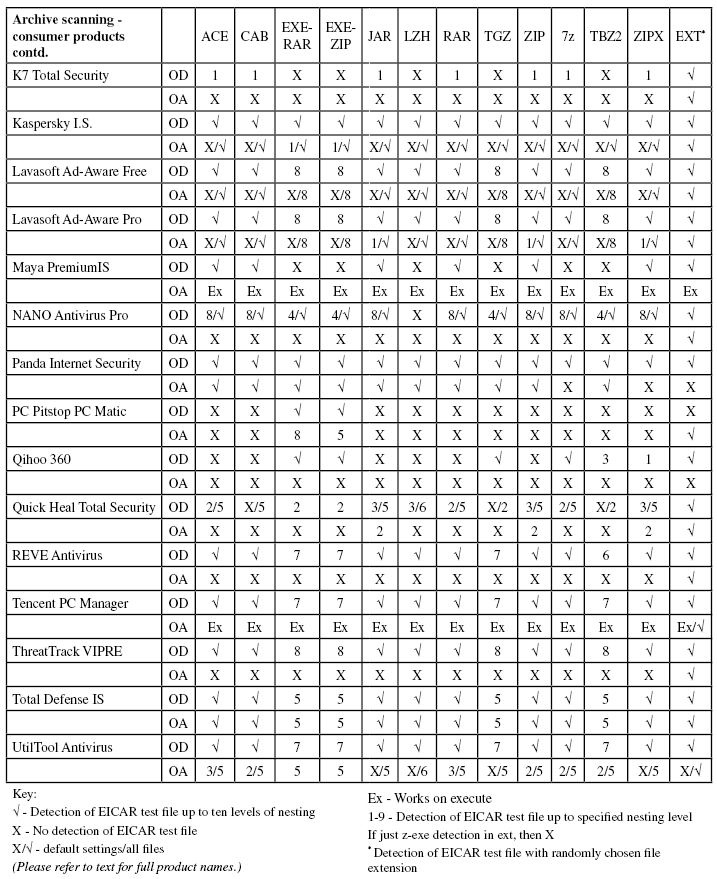
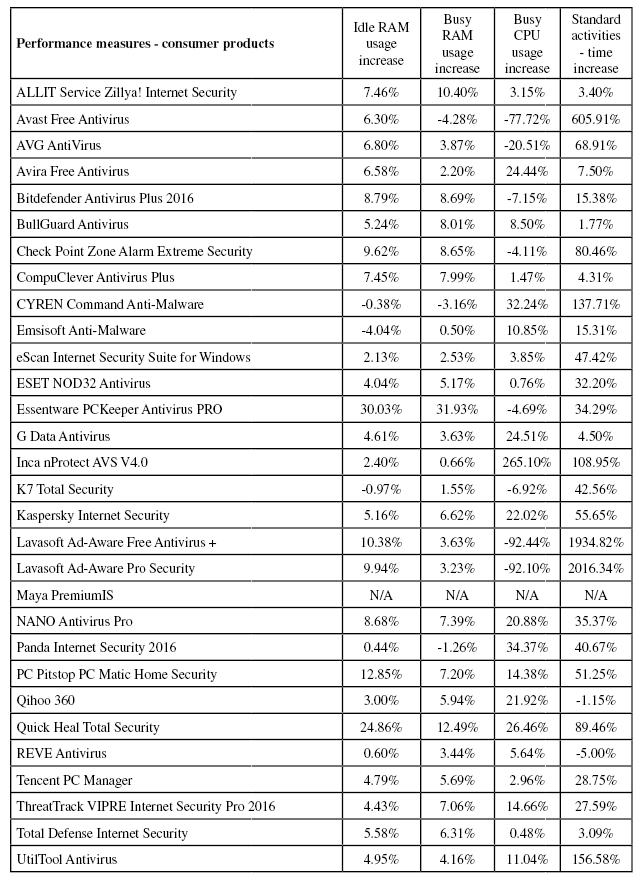
Consumer products
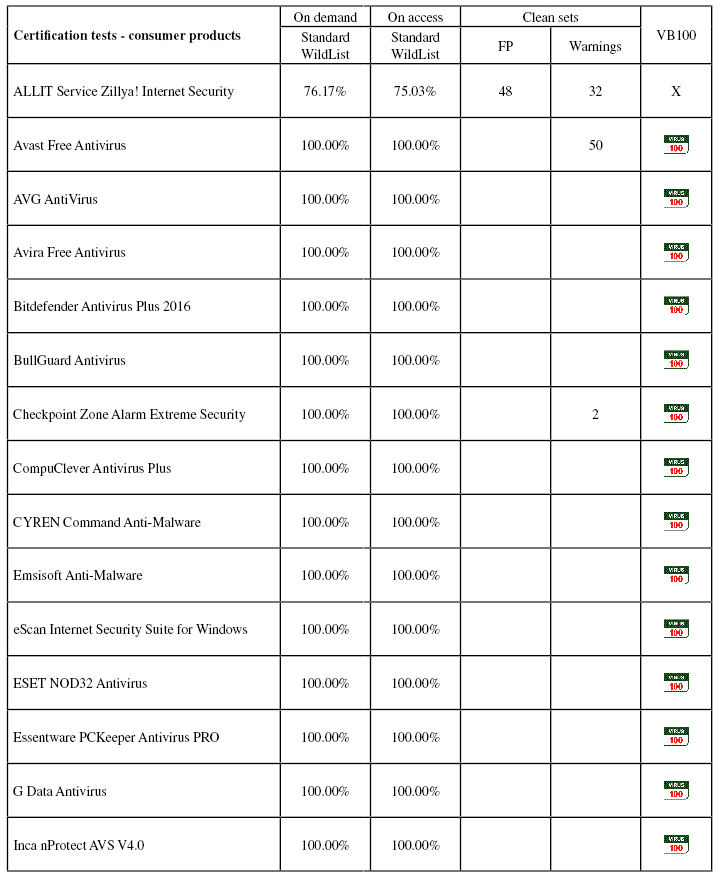
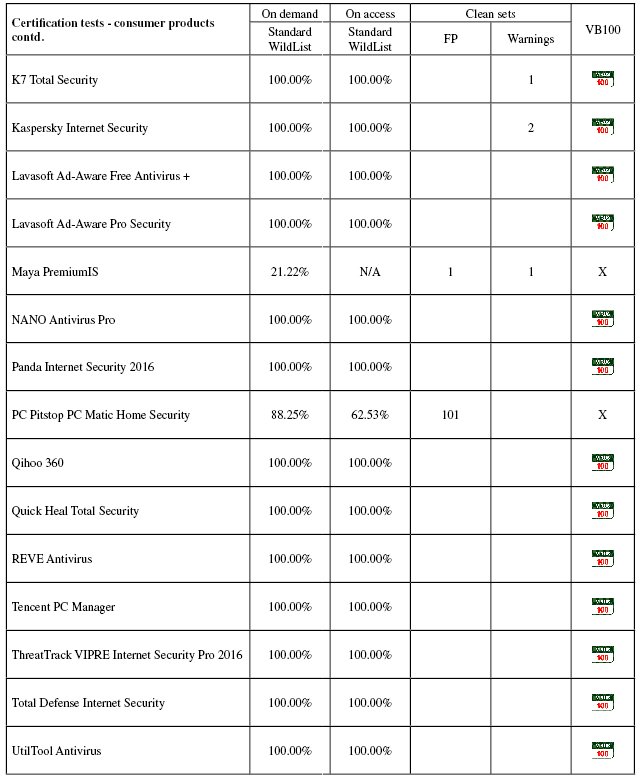
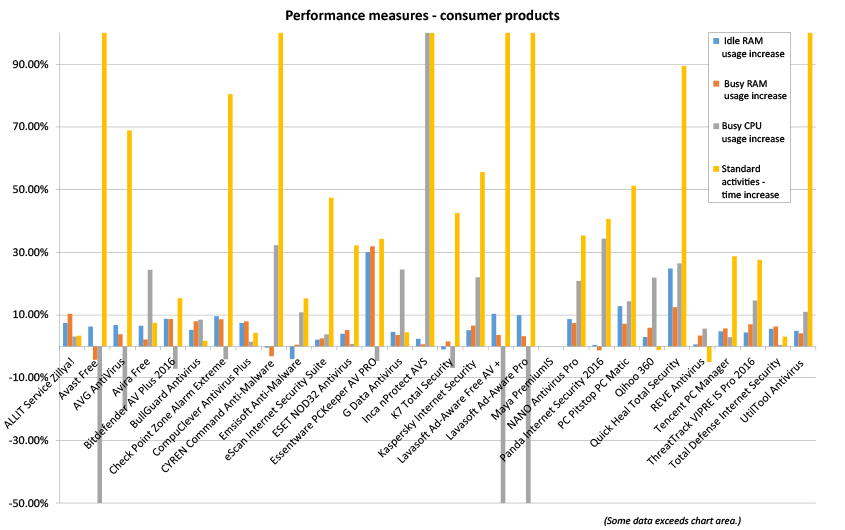
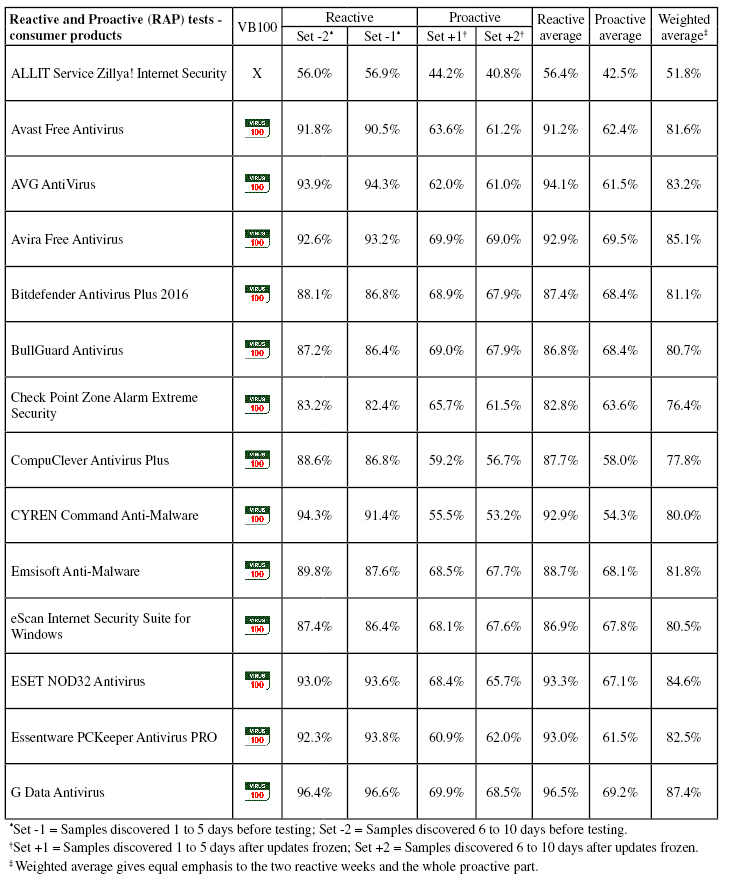
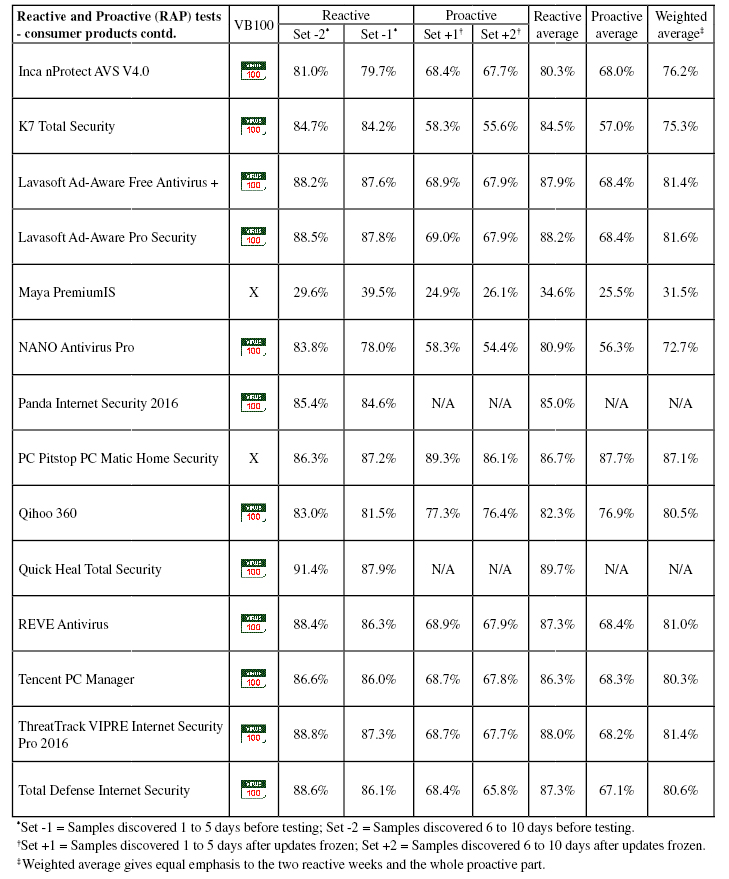
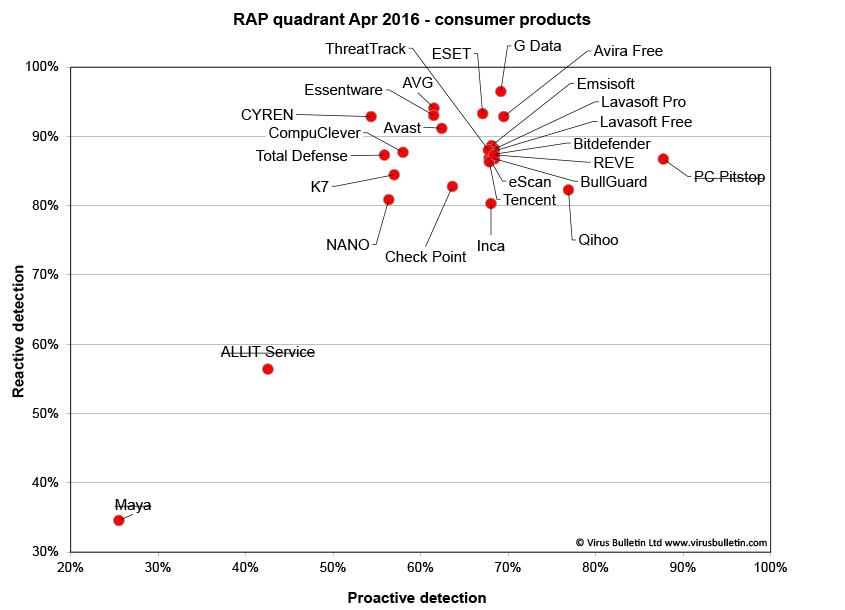
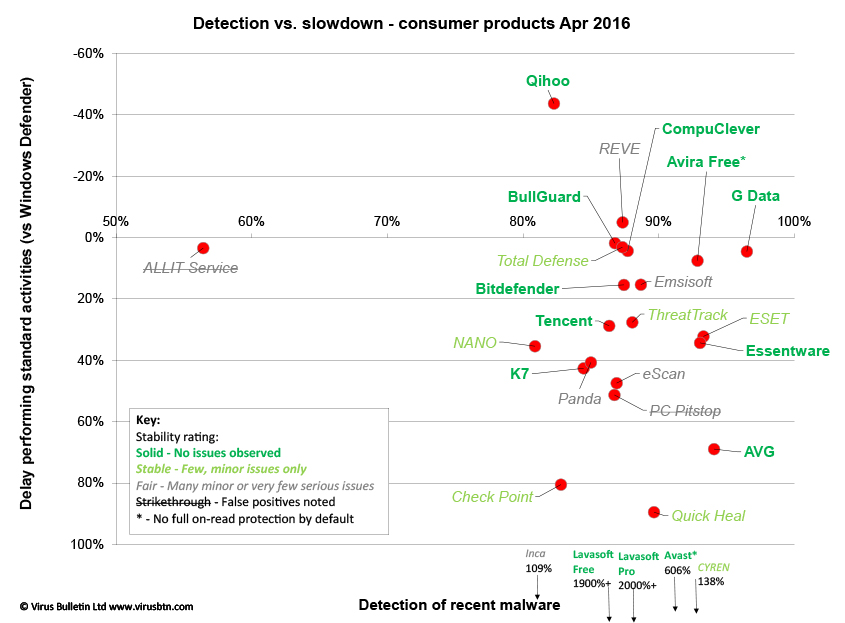
Conclusions
This test report has been somewhat abbreviated to help clear a backlog, but hopefully includes enough detail to give some guidance as to which products are performing well and which need improvement. We saw another good rate of passes in this comparative, with a few products clearly falling short of the required standard, a couple hit by bouts of false positives upsetting otherwise good scores, and a couple very near but not quite there. For the most part though, we saw impressive performances, with speed measures particularly encouraging on this now well‑established platform.
The RAP scores were a little below the levels we normally see, which may be due to some adjustments to the way the sets are compiled, tweaking our methods for determining the significance of samples at selection time. In the very near future we hope to move this entire process over to the AMTSO RTTL (Real-Time Threat List), which should reduce the workload involved in determining how widespread a given sample is, as well as making it significantly more accurate. This will not be in the next test, which should closely follow the publication of this report, but should we hope be ready in time for our August comparative on Windows 10.
Technical details
All tests were run on identical systems with AMD A6-3670K Quad Core 2.7GHz processors, 4GB DUAL DDR3 1600MHz RAM, dual 500GB and 1TB SATA hard drives and gigabit networking, running Microsoft Windows 8.1 64-bit Professional Edition.
, https://itretecon.site123.me/blog/license-key-foxit-pdf-editor-v221 license_key_foxit_pdf_editor_v2.2.1, https://chalgaiconsfidd.site123.me/blog/keygen-rpg-maker-xp keygen_rpg_maker_xp, https://anerasas.site123.me/blog/mp3-convert-download mp3_convert_download, https://reastaigelri.site123.me/blog/minecraft-story-mode-season-2-free-download-pc-windows-10 minecraft_story_mode_season_2_free_download_pc_windows_10, https://ecregarvou.site123.me/blog/life-is-strange-before-the-storm-limited-edition-multi8-repack-by-fitgirl life_is_strange_before_the_storm_limited_edition_multi8_repack_by_fitgirl, https://gladevhearhie.site123.me/blog/msn-messenger-download-for-windows-10 msn_messenger_download_for_windows_10, https://testsurunpay.site123.me/versions/2/wizard/modules/blog/addItem.php norma_iso_9001_vers達o_2015_pdf_gratis, https://baphimerxi.site123.me/blog/mobile-games-free-download-2017 mobile_games_free_download_2017, https://testsurunpay.site123.me/blog/need-for-speed-payback-pc-download-rg-mechanics need_for_speed_payback_pc_download_rg_mechanics, https://agestwojac.site123.me/blog/microsoft-excel-2013-product-key-for-windows-10 microsoft_excel_2013_product_key_for_windows_10, https://testsurunpay.site123.me/blog/microsoft-windows-7-product-key-sticker microsoft_windows_7_product_key_sticker, https://itretecon.site123.me/blog/minecraft-medieval-house-schematics-download minecraft_medieval_house_schematics_download, https://ecregarvou.site123.me/blog/minecraft-113-download-unblocked-at-school minecraft_1.13_download_unblocked_at_school, https://enkolobspo.site123.me/blog/lil-durk-what-if-download lil_durk_what_if_download, https://niricawist.site123.me/blog/minecraft-unblocked-sweet-and-awesome-jar-download minecraft_unblocked_sweet_and_awesome_jar_download, https://atmachlega.site123.me/blog/nero-6-download-free-windows-8 nero_6_download_free_windows_8, https://quiquatkade.site123.me/blog/iso-7975 iso_7975, https://provarlame.site123.me/blog/iso-5001-lead-auditor-training iso_5001_lead_auditor_training, https://littmusccockdan.site123.me/blog/iso-50001-audit-checklist-excel iso_50001_audit_checklist_excel, https://agestwojac.site123.me/blog/kick-telugu-full-movie-free-download-hd-720p kick_telugu_full_movie_free_download_hd_720p, https://reastaigelri.site123.me/blog/mahanati-watch-online-movierulz mahanati_watch_online_movierulz, https://fanjakipart.site123.me/blog/mcpe-apk-xbox mcpe_apk_xbox, https://provarlame.site123.me/blog/movie-magic-torrent movie_magic_torrent, https://atmachlega.site123.me/blog/league-of-stickman-apk-572 league_of_stickman_apk_5.7.2, https://reacalcountfor.site123.me/blog/melodyne-editor-keygen melodyne_editor_keygen, https://itretecon.site123.me/blog/midi-pjesme-download midi_pjesme_download, https://mulnylpphoca.site123.me/blog/minecraft-optifine-1131-download minecraft_optifine_1.13.1_download, https://enbotooco.site123.me/blog/norton-anthology-of-english-literature-10th-edition-volume-2 norton_anthology_of_english_literature_10th_edition_volume_2, https://baphimerxi.site123.me/blog/ms-office-2016-activation-crack-torrent ms_office_2016_activation_crack_torrent, https://fanjakipart.site123.me/blog/lenovo-thinkcentre-drivers-for-windows-xp-32-bit lenovo_thinkcentre_drivers_for_windows_xp_32_bit, https://xagdingvingcal.site123.me/blog/katcr-link kat.cr_link, https://kargeguarke.site123.me/blog/minecraft-mod-16-4-optifine minecraft_mod_1.6_4_optifine, https://baphimerxi.site123.me/blog/lol-limited-edition-glitter-series lol_limited_edition_glitter_series, https://wanemeaco.site123.me/blog/movavi-video-converter-10-full movavi_video_converter_10_full, https://tiwellleled.site123.me/blog/most-popular-movie-rentals-2017 most_popular_movie_rentals_2017, https://reastaigelri.site123.me/blog/ivkova-slava-film-download-free ivkova_slava_film_download_free, https://xagdingvingcal.site123.me/blog/malayalam-movie-download-app-free malayalam_movie_download_app_free, https://niricawist.site123.me/blog/microsoft-download-windows-7-with-product-key microsoft_download_windows_7_with_product_key, https://lumperbrenew.site123.me/blog/microsoft-81-product-key-free microsoft_8.1_product_key_free, https://tingsmearakuap.site123.me/blog/motogp-apk-mod-offline motogp_apk_mod_offline, https://testsurunpay.site123.me/blog/my-singing-monsters-apk-mod-218 my_singing_monsters_apk_mod_2.1.8, https://enbotooco.site123.me/blog/kaspersky-internet-security-2013-activation-code kaspersky_internet_security_2013_activation_code,
2019-06-21 03:53:51 Buupsdcz
, https://riopretingi.kinja.com/five-star-hotel-background-music-download-1835678193 five_star_hotel_background_music_download, https://enicefip.kinja.com/clash-of-clans-full-mod-apk-download-1835696264 clash_of_clans_full_mod_apk_download, https://levidowpe.kinja.com/minecraft-ps3-maps-download-eu-1835674889 minecraft_ps3_maps_download_eu, https://daroformpom.kinja.com/samsung-galaxy-tab-a-8-0-keyboard-1835681389 samsung_galaxy_tab_a_8.0_keyboard, https://immordored.kinja.com/download-files2-info-activ2-windows-loader-1835682539 download_files2_info_activ2_windows_loader, https://protsehtentves.kinja.com/scary-movie-2-download-in-tamil-1835680584 scary_movie_2_download_in_tamil, https://cheersenewstor.kinja.com/1967-canadian-dollar-bill-without-serial-number-1835691791 1967_canadian_dollar_bill_without_serial_number, https://naimiretni.kinja.com/game-pc-free-download-gta-san-andreas-1835684952 game_pc_free_download_gta_san_andreas, https://ethcenlejohn.kinja.com/download-roehsoft-ram-expander-swap-v3-36-cracked-apk-1835694802 download_roehsoft_ram_expander_(swap)_v3.36_cracked_apk, https://levidowpe.kinja.com/exo-ko-ko-bop-download-1835674085 exo_ko_ko_bop_download, https://stancapdodi.kinja.com/gta-5-online-heists-loading-time-1835685363 gta_5_online_heists_loading_time, https://ovinivpea.kinja.com/do-prada-wallets-have-serial-numbers-1835670885 do_prada_wallets_have_serial_numbers, https://lisigitab.kinja.com/download-pokemon-soul-silver-emulator-1835692795 download_pokemon_soul_silver_emulator, https://lisarebil.kinja.com/youtube-downloader-cnet-windows-10-1835676195 youtube_downloader_cnet_windows_10, https://ertihybme.kinja.com/gta-san-andreas-download-apk-data-aptoide-1835679633 gta_san_andreas_download_apk_data_aptoide, https://rtunwabhartstan.kinja.com/youtube-mp3-audio-songs-free-download-softonic-1835676497 youtube_mp3_audio_songs_free_download_-_softonic, https://amitunfi.kinja.com/free-disney-star-wars-svg-1835686405 free_disney_star_wars_svg, https://graphcatwinkdewd.kinja.com/download-microsoft-windows-8-1-for-free-1835697957 download_microsoft_windows_8.1_for_free, https://naimiretni.kinja.com/fifa-15-demo-download-android-1835684009 fifa_15_demo_download_android, https://settretitic.kinja.com/locke-key-pilot-download-1835682708 locke_&_key_pilot_download, https://tiditeran.kinja.com/city-car-driving-home-edition-activation-key-free-1835683901 city_car_driving_home_edition_activation_key_free, https://aswrithampcheck.kinja.com/download-office-2016-full-crack-cho-macbook-1835672258 download_office_2016_full_crack_cho_macbook, https://lisarebil.kinja.com/microsoft-office-excel-2010-for-mac-free-download-full-1835677057 microsoft_office_excel_2010_for_mac_free_download_full_version, https://commumentcon.kinja.com/download-winx-free-mp4-to-avi-converter-1835676216 download_winx_free_mp4_to_avi_converter, https://gepordopar.kinja.com/hellblade-senuas-sacrifice-vr-edition-steam-key-1835689841 hellblade_senuas_sacrifice_vr_edition_steam_key, https://vervagarbthe.kinja.com/drivers-license-renewal-az-locations-1835670409 drivers_license_renewal_az_locations, https://immordored.kinja.com/titanium-backup-pro-key-root-6-0-5-1-apk-1835682316 titanium_backup_pro_key_笘・root_6.0.5.1_apk, https://tiebreasphihost.kinja.com/sallys-salon-online-free-full-version-1835670101 sallys_salon_online_free_full_version, https://badutidam.kinja.com/photosmart-plus-b210-driver-mac-1835688226 photosmart_plus_b210_driver_mac, https://mentoifaro.kinja.com/counter-strike-aimbot-download-2015-1835679495 counter_strike_aimbot_download_2015, https://amitunfi.kinja.com/north-carolina-driving-test-questions-and-answers-1835686259 north_carolina_driving_test_questions_and_answers, https://levidowpe.kinja.com/reaper-no-asio-drivers-found-1835674494 reaper_no_asio_drivers_found, https://vervagarbthe.kinja.com/counter-strike-1-6-download-free-full-version-1835670564 counter_strike_1.6_download_free_full_version, https://commumentcon.kinja.com/download-galaxy-reavers-mod-apk-revdl-1835676569 download_galaxy_reavers_mod_apk_revdl, https://balmabarla.kinja.com/kaspersky-total-security-2018-activation-code-youtube-1835688618 kaspersky_total_security_2018_activation_code_youtube, https://sverincolcha.kinja.com/r6-siege-complete-edition-ps4-1835673898 r6_siege_complete_edition_ps4, https://riopretingi.kinja.com/the-martian-full-movie-in-hindi-download-kickass-1835678093 the_martian_full_movie_in_hindi_download_kickass, https://lisigitab.kinja.com/uniontown-pa-drivers-license-center-1835693334 uniontown_pa_drivers_license_center, https://rtunwabhartstan.kinja.com/spotify-premium-apk-for-ios-12-1835676258 spotify_premium_apk_for_ios_12, https://ropalrefeed.kinja.com/universal-keygen-generator-autocad-2014-1835691039 universal_keygen_generator_autocad_2014, https://naimiretni.kinja.com/iphone-5c-stuck-in-dfu-mode-black-screen-1835684150 iphone_5c_stuck_in_dfu_mode_black_screen, https://rinewardgu.kinja.com/what-time-does-the-gta-5-dlc-come-out-1835698613 what_time_does_the_gta_5_dlc_come_out, https://balmabarla.kinja.com/dell-drivers-update-utility-download-1835687277 dell_drivers_update_utility_download, https://buslabourgirl.kinja.com/windows-7-ultimate-64-bit-iso-tpb-1835691016 windows_7_ultimate_64_bit_iso_tpb, https://partusimpdow.kinja.com/sound-card-for-pc-windows-7-free-download-1835689324 sound_card_for_pc_windows_7_free_download, https://apdistingtes.kinja.com/why-cant-i-play-minecraft-realms-1835669031 why_cant_i_play_minecraft_realms, https://poundvetaboun.kinja.com/download-coreldraw-x-14-full-version-1835698206 download_coreldraw_x_14_full_version,
2019-06-21 10:04:53 Yyoompyk
, https://www.podomatic.com/podcasts/trumecdauro/episodes/2019-06-20T06_19_20-07_00 sony_vegas_logo_intro_templates_free_download, https://www.podomatic.com/podcasts/onkaisigbi/episodes/2019-06-20T17_17_51-07_00 sanju_hindi_movie_torrent_file_download, https://www.podomatic.com/podcasts/meailoachaeprot/episodes/2019-06-20T14_40_31-07_00 rsa_2048_keygen, https://www.podomatic.com/podcasts/onkaisigbi/episodes/2019-06-20T17_10_31-07_00 quick_logo_designer_free_registration_key, https://www.podomatic.com/podcasts/trumecdauro/episodes/2019-06-20T06_17_45-07_00 pdf_viewer_apk, https://www.podomatic.com/podcasts/rejevefe/episodes/2019-06-20T09_00_33-07_00 pinnacle_studio_12_ultimate_free_download_full_version, https://www.podomatic.com/podcasts/gradunvibdist/episodes/2019-06-20T08_29_41-07_00 purenet_cable, https://www.podomatic.com/podcasts/inephinmi/episodes/2019-06-20T08_24_06-07_00 pinterest_download_for_android, https://www.podomatic.com/podcasts/stewylsigheart/episodes/2019-06-20T16_19_59-07_00 polyboard_activation_key, https://www.podomatic.com/podcasts/cathemati/episodes/2019-06-20T13_53_41-07_00 rebuild_3_apk_ios, https://www.podomatic.com/podcasts/eclomusign/episodes/2019-06-20T07_48_40-07_00 radio_removal_tool_supercheap_auto, https://www.podomatic.com/podcasts/funcderahand/episodes/2019-06-20T11_12_16-07_00 order_vuse_ciro_online, https://www.podomatic.com/podcasts/heffeterning/episodes/2019-06-20T09_55_05-07_00 sinister_2_download_subtitles, https://www.podomatic.com/podcasts/charakabo/episodes/2019-06-20T11_17_34-07_00 pirate_bay_for_textbooks, https://www.podomatic.com/podcasts/llowecandi/episodes/2019-06-20T04_23_19-07_00 super_mario_run_hack_apk_3.0.6, https://www.podomatic.com/podcasts/eclomusign/episodes/2019-06-20T07_32_37-07_00 showbox_apk_install_greyed_out, https://www.podomatic.com/podcasts/postrakundner/episodes/2019-06-20T03_53_55-07_00 skills_worksheet_active_reading_section_1_what_is_a_biome_answer_key, https://www.podomatic.com/podcasts/binsmilinon/episodes/2019-06-20T12_26_40-07_00 sorry_for_the_wait_2_free_download, https://www.podomatic.com/podcasts/predbumcitac/episodes/2019-06-20T13_28_13-07_00 super_mario_pc_free_download, https://www.podomatic.com/podcasts/rejevefe/episodes/2019-06-20T08_46_25-07_00 psiphon_pro_premium_apkpure, https://www.podomatic.com/podcasts/postrakundner/episodes/2019-06-20T03_52_20-07_00 spacedesk_old_apk, https://www.podomatic.com/podcasts/meailoachaeprot/episodes/2019-06-20T14_08_31-07_00 online_key_duplication, https://www.podomatic.com/podcasts/postrakundner/episodes/2019-06-20T03_22_17-07_00 prime_video_apk_file_for_mi_tv, https://www.podomatic.com/podcasts/lighpeclicor/episodes/2019-06-20T07_34_44-07_00 photoshop_older_version_free, https://www.podomatic.com/podcasts/illidelmo/episodes/2019-06-20T12_01_57-07_00 oracle_vm_virtualbox_iso_image, https://www.podomatic.com/podcasts/onkaisigbi/episodes/2019-06-20T16_17_22-07_00 smule_modified_apk, https://www.podomatic.com/podcasts/meailoachaeprot/episodes/2019-06-20T13_24_49-07_00 phone_visibility_galaxy_s7, https://www.podomatic.com/podcasts/illidelmo/episodes/2019-06-20T11_24_19-07_00 spartan_bodyweight_pro_apk_cracked, https://www.podomatic.com/podcasts/stewylsigheart/episodes/2019-06-20T17_22_57-07_00 rootkit_virus_in_crack_software, https://www.podomatic.com/podcasts/gradunvibdist/episodes/2019-06-20T09_28_38-07_00 router_keygen_app_download, https://www.podomatic.com/podcasts/elmiskula/episodes/2019-06-20T13_07_44-07_00 play_minecraft_on_ubuntu_18.04, https://www.podomatic.com/podcasts/hilttelecgers/episodes/2019-06-20T04_31_07-07_00 snes_super_nintendo_emulator_download, https://www.podomatic.com/podcasts/llowecandi/episodes/2019-06-20T04_25_58-07_00 rs_partition_recovery_2.3_registration_key, https://www.podomatic.com/podcasts/gradunvibdist/episodes/2019-06-20T08_45_05-07_00 prisma_apk_latest_version, https://www.podomatic.com/podcasts/gradunvibdist/episodes/2019-06-20T09_05_17-07_00 rubymine_keygen_mac, https://www.podomatic.com/podcasts/meailoachaeprot/episodes/2019-06-20T13_41_29-07_00 powerpoint_2017_download_free_full_version, https://www.podomatic.com/podcasts/trumecdauro/episodes/2019-06-20T07_05_07-07_00 super_mario_kart_emulator_unblocked, https://www.podomatic.com/podcasts/dietreatexme/episodes/2019-06-20T17_27_29-07_00 richard_burns_rally_tracks_download, https://www.podomatic.com/podcasts/siolensdawdcer/episodes/2019-06-20T04_52_35-07_00 saucony_ride_iso_weight, https://www.podomatic.com/podcasts/charakabo/episodes/2019-06-20T11_42_47-07_00 repelisplus_apk_hack_2018, https://www.podomatic.com/podcasts/rejevefe/episodes/2019-06-20T08_47_28-07_00 samsung_arc_problems, https://www.podomatic.com/podcasts/meailoachaeprot/episodes/2019-06-20T13_38_53-07_00 product_key_office_2013_pro, https://www.podomatic.com/podcasts/funcderahand/episodes/2019-06-20T11_02_15-07_00 talend_download_file_from_sharepoint, https://www.podomatic.com/podcasts/eclomusign/episodes/2019-06-20T07_39_43-07_00 photoshop_6_serial, https://www.podomatic.com/podcasts/funcderahand/episodes/2019-06-20T11_15_44-07_00 samsung_s5610_flash_loader_download,
2019-06-21 12:12:53 Kinjfmfa
, https://pes-2016-data-pack-download-rpp.peatix.com/ pes-2016-data-pack-download, https://microsoft-office-2007-ac-wqq.peatix.com/ microsoft-office-2007-ac, https://biology-the-essentials-3-qh.peatix.com/ biology-the-essentials-3, https://what-does-cpa-stand-for-tp.peatix.com/ what-does-cpa-stand-for, https://gbc-emulator-pc-download-csd.peatix.com/ gbc-emulator-pc-download, https://best-free-iso-jgz.peatix.com/ best-free-iso, https://where-to-buy-rpg-books-mmw.peatix.com/ where-to-buy-rpg-books, https://nero-7-ultra-s-ikh.peatix.com/ nero-7-ultra-s, https://windows-vista-iso-files-in.peatix.com/ windows-vista-iso-files, https://hp-pavilion-dm-zlq.peatix.com/ hp-pavilion-dm, https://geometry-dash-2-mhh.peatix.com/ geometry-dash-2, https://ct-drivers-lic-ep.peatix.com/ ct-drivers-lic, https://russian-movies-2018-fr-uc.peatix.com/ russian-movies-2018-fr, https://popular-websites-from-the-ua.peatix.com/ popular-websites-from-the, https://fl-studio-9-k-udf.peatix.com/ fl-studio-9-k, https://minecraft-64-lcu.peatix.com/ minecraft-64, https://permanently-act-sg.peatix.com/ permanently-act, https://cyberlink-powercinema-6-s-st.peatix.com/ cyberlink-powercinema-6-s, https://bypass-gravity-forms-license-ke-zv.peatix.com/ bypass-gravity-forms-license-ke, https://18-wheels-of-steel-e-ql.peatix.com/ 18-wheels-of-steel-e, https://activate-windows-7-h-nv.peatix.com/ activate-windows-7-h, https://vegas-pro-14-edit-vs-vegas-bw.peatix.com/ vegas-pro-14-edit-vs-vegas, https://job-for-forklift-dr-yhg.peatix.com/ job-for-forklift-dr, https://respironics-cpap-serial-numbe-uw.peatix.com/ respironics-cpap-serial-numbe, https://download-fifa-07-to-aty.peatix.com/ download-fifa-07-to, https://dragon-city-ha-qff.peatix.com/ dragon-city-ha, https://the-circle-2017-torrent-ezy.peatix.com/ the-circle-2017-torrent, https://apk-editor-pr-mix.peatix.com/ apk-editor-pr, https://pdf-architect-4-key-free-sdn.peatix.com/ pdf-architect-4-key-free, https://until-dawn-pc-free-ltw.peatix.com/ until-dawn-pc-free, https://injustice-2-apk-mod-ug.peatix.com/ injustice-2-apk-mod, https://nitro-pro-enterprise-12-keyge-rw.peatix.com/ nitro-pro-enterprise-12-keyge, https://bs-player-free-down-ucd.peatix.com/ bs-player-free-down, https://adobe-photoshop-cs3-to.peatix.com/ adobe-photoshop-cs3, https://forza-motorsport-ff.peatix.com/ forza-motorsport, https://free-download-showbox-rs.peatix.com/ free-download-showbox, https://photoshop-license-key-gen-pwn.peatix.com/ photoshop-license-key-gen, https://download-rainbow-six-siege-ubis-ru.peatix.com/ download-rainbow-six-siege-ubis, https://kms-activator-download-office-2-gto.peatix.com/ kms-activator-download-office-2, https://download-zip-7-f-ixr.peatix.com/ download-zip-7-f, https://flex-shaft-vs-stiff-shaft-driv-zw.peatix.com/ flex-shaft-vs-stiff-shaft-driv, https://k7-total-security-setu-dq.peatix.com/ k7-total-security-setu, https://hp-photosmart-d1-gfn.peatix.com/ hp-photosmart-d1, https://google-voice-apk-dow-dlh.peatix.com/ google-voice-apk-dow, https://dubo-gaming-emulator-apk-ego.peatix.com/ dubo-gaming-emulator-apk, https://skylanders-spy-vln.peatix.com/ skylanders-spy, https://ppsspp-gold-psp-emulator-for-pc-bmd.peatix.com/ ppsspp-gold-psp-emulator-for-pc, https://registration-ke-iib.peatix.com/ registration-ke,
2019-06-21 12:55:25 Auwaoxyc
, https://www.f6s.com/howtodownloadwindows10isofileandinstall how_to_download_windows_10_iso_file_and_install, https://www.f6s.com/installdolphinemulatoronretropie install_dolphin_emulator_on_retropie, http://archive.vn/vcoDa gta_v_gangster_cars, https://www.f6s.com/fortnitehacksforsaleps4 fortnite_hacks_for_sale_ps4, http://archive.li/GrzJQ ios_7_music_player_apk, http://archive.vn/onP0B free_aimbot, https://www.f6s.com/howtofindhardwareidforavatarkeygen how_to_find_hardware_id_for_avatar_keygen, https://www.f6s.com/googleplaystoreapkfreedownloadgames google_play_store_apk_free_download_games, https://www.f6s.com/funnynamesfordriversed funny_names_for_drivers_ed, https://www.f6s.com/instalarapkenandroidwear instalar_apk_en_android_wear, https://www.f6s.com/heroesofmightandmagic3downloadfreefullversioncz heroes_of_might_and_magic_3_download_free_full_version_cz, https://www.f6s.com/fonepawiphonedatarecoveryregistrationcode fonepaw_iphone_data_recovery_registration_code, http://archive.fo/5Llh1 go_locker_apk_versions, http://archive.li/Jlnxv guild_wars_2_download_client, https://www.f6s.com/inlivingcolortorrents in_living_color_torrents, https://www.f6s.com/instagramdownloadvideoextension instagram_download_video_extension, http://archive.li/dHYhR instagram_edit_challenge, https://www.f6s.com/hillclimbracinghackmodapkhome hill_climb_racing_hack_mod_apk_home, https://www.f6s.com/installfreewindows10onmac install_free_windows_10_on_mac, https://www.f6s.com/freedownloadnewpcgamesfullversion free_download_new_pc_games_full_version, https://www.f6s.com/inceptionenglishfullmoviedownloadtorrent inception_english_full_movie_download_torrent, http://archive.vn/8mdaA fast_furious_6_watch_online_123movies, https://www.f6s.com/ipvanishvpncracktorrent ipvanish_vpn_+_crack_torrent, http://archive.li/NnRAG free_windows_7_games_free_download, https://www.f6s.com/gtavicecitykillingsonny gta_vice_city_killing_sonny, https://www.f6s.com/gooddriversschoolmississauga good_drivers_school_mississauga, https://www.f6s.com/gta5downloadandroidfreepc gta_5_download_android_free_pc, http://archive.fo/atiE4 fedex_driver_jobs_uk, https://www.f6s.com/iso18003 iso_18003, https://www.f6s.com/goddesskissmodapkunlimitedmoney goddess_kiss_mod_apk_unlimited_money, https://www.f6s.com/idopeapkdownloadforpc idope_apk_download_for_pc, https://www.f6s.com/ironman3pcgamefreedownloadfullversionsoftonic iron_man_3_pc_game_free_download_full_version_softonic, https://www.f6s.com/freedownloadablegamesforpctoplayoffline free_downloadable_games_for_pc_to_play_offline, http://archive.vn/sHTxh free_terrarium_tv_apk, http://archive.is/vOTpr fts_15_mod_apk_data_download, https://www.f6s.com/freecs6serialnumbergenerator free_cs6_serial_number_generator, https://www.f6s.com/freetorrentsmoviesdownload free_torrents_movies_download, https://www.f6s.com/freedownloadadobephotoshopcs5setup free_download_adobe_photoshop_cs5_setup, http://archive.li/6czTP futurama_worlds_of_tomorrow_mod_apk_2019, https://www.f6s.com/hidetorrentingfree hide_torrenting_free, https://www.f6s.com/gigabytedchdrivers gigabyte_dch_drivers, http://archive.vn/nswWv gmod_for_android_apk_download, http://archive.is/uvZC1 good_torrenting_software, https://www.f6s.com/flashplayerofflineinstallerdownload flash_player_offline_installer_download, https://www.f6s.com/fnaf6apkdownloadaptoide fnaf_6_apk_download_aptoide, https://www.f6s.com/genymotionfullbagas31 genymotion_full_bagas31,
2019-06-21 14:13:20 Ukizmdvh
, https://rhapcomulja.site123.me/blog/iso-iec-11801-1 iso/iec_11801-1, https://speedearviena.site123.me/blog/launch-downloads-app launch_downloads_app, https://rhapcomulja.site123.me/blog/libzipso libzip.so, https://rhapcomulja.site123.me/blog/miui-themes-not-downloading miui_themes_not_downloading, https://speedearviena.site123.me/blog/office-2016-permanent-activator-ultimate-v11 office_2016_permanent_activator_ultimate_v1.1, https://peloceren.site123.me/blog/metro-exodus-download-patch metro_exodus_download_patch, https://camrehouda.site123.me/blog/multicraft-license-key-free multicraft_license_key_free, https://plasymalas.site123.me/blog/legacy-curse-client-download legacy_curse_client_download, https://ungogorbirth.site123.me/blog/miracle-227a-loader-download miracle_227a_loader_download, https://tiobrigexnjum.site123.me/blog/minecraft-pe-120-download-apk minecraft_pe_12.0_download_apk, https://speedearviena.site123.me/blog/license-definition-black-law-dictionary license_definition_black_law_dictionary, https://mumtelanha.site123.me/blog/lantern-apk lantern_apk, https://feahasslarback.site123.me/blog/lenovo-mac-address-from-serial-number lenovo_mac_address_from_serial_number, https://bravlumoter.site123.me/blog/new-tamil-movie-download-in-tamilrockers new_tamil_movie_download_in_tamilrockers, https://crenperotic.site123.me/blog/minecraft-demosuz-indir-1122 minecraft_demosuz_indir_1.12.2, https://sighrihensti.site123.me/blog/kaspersky-total-security-2017-key kaspersky_total_security_2017_key, https://onswelarac.site123.me/blog/mount-and-blade-serial-key-youtube mount_and_blade_serial_key_youtube, https://diefridisla.site123.me/blog/kgf-full-movie-torrent-download-in-hindi kgf_full_movie_torrent_download_in_hindi, https://ungogorbirth.site123.me/blog/nox-app-player-android-44-2-emulator-for-pc nox_app_player_android_4.4_2_emulator_for_pc, https://bidamrehips.site123.me/blog/minecraft-full-version-pc-2019 minecraft_full_version_pc_2019, https://tempboshali.site123.me/blog/kendall-and-kylie-hack-2019 kendall_and_kylie_hack_2019, https://camrehouda.site123.me/blog/iso-9001-iso-27001-integration iso_9001_&_iso_27001_integration, https://mumtelanha.site123.me/blog/mcpe-block-launcher-apk mcpe_block_launcher_apk, https://tiobrigexnjum.site123.me/blog/konica-minolta-drivers-mac-el-capitan konica_minolta_drivers_mac_el_capitan, https://rhapcomulja.site123.me/blog/iso-final-fantasy-xii-international-zodiac-job-system iso_final_fantasy_xii_international_zodiac_job_system, https://crenperotic.site123.me/blog/logitech-k400-driver-software logitech_k400_driver_software, https://efapprosim.site123.me/blog/nwn-2-patch-download nwn_2_patch_download, https://speedearviena.site123.me/blog/ml1710-drivers ml1710_drivers, https://taupregteicomp.site123.me/blog/matlab-2013-free-download-with-crack-64-bit matlab_2013_free_download_with_crack_64_bit, https://taupregteicomp.site123.me/blog/music-making-games-unblocked music_making_games_unblocked, https://neumisstravin.site123.me/blog/mobo-market-apk-download mobo_market_apk_download, https://neumisstravin.site123.me/blog/microsoft-office-2007-torrent-crack microsoft_office_2007_torrent_crack, https://erpfafonti.site123.me/blog/norma-iso-10013-pdf-espaB1ol norma_iso_10013_pdf_espa単ol, https://hardcredenprop.site123.me/blog/minecraft-pe-sao-map-download minecraft_pe_sao_map_download, https://arpenvasel.site123.me/blog/iso-file-to-dvd-windows-10 iso_file_to_dvd_windows_10, https://cerncecygag.site123.me/blog/kim-hackney-goldcorp kim_hackney_goldcorp, https://cerncecygag.site123.me/blog/moto-racer-4-free-download moto_racer_4_free_download, https://bidamrehips.site123.me/blog/megadrive-emulator-android-apk megadrive_emulator_android_apk, https://parkbhagearno.site123.me/blog/mirror-apk-mod mirror_apk_mod, https://guetepkela.site123.me/blog/mac-linksys-router-setup mac_linksys_router_setup, https://diefridisla.site123.me/blog/ms-product-key-2019 ms_product_key_2019, https://peloceren.site123.me/blog/norton-internet-security-2012-product-key-free norton_internet_security_2012_product_key_free, https://peloceren.site123.me/blog/marshall-county-drivers-license marshall_county_drivers_license, https://binabwealthten.site123.me/blog/movie-app-hd-pro-apk movie_app_hd_pro_apk,
2019-06-21 14:13:37 Ukizmdvh
, https://rhapcomulja.site123.me/blog/iso-iec-11801-1 iso/iec_11801-1, https://speedearviena.site123.me/blog/launch-downloads-app launch_downloads_app, https://rhapcomulja.site123.me/blog/libzipso libzip.so, https://rhapcomulja.site123.me/blog/miui-themes-not-downloading miui_themes_not_downloading, https://speedearviena.site123.me/blog/office-2016-permanent-activator-ultimate-v11 office_2016_permanent_activator_ultimate_v1.1, https://peloceren.site123.me/blog/metro-exodus-download-patch metro_exodus_download_patch, https://camrehouda.site123.me/blog/multicraft-license-key-free multicraft_license_key_free, https://plasymalas.site123.me/blog/legacy-curse-client-download legacy_curse_client_download, https://ungogorbirth.site123.me/blog/miracle-227a-loader-download miracle_227a_loader_download, https://tiobrigexnjum.site123.me/blog/minecraft-pe-120-download-apk minecraft_pe_12.0_download_apk, https://speedearviena.site123.me/blog/license-definition-black-law-dictionary license_definition_black_law_dictionary, https://mumtelanha.site123.me/blog/lantern-apk lantern_apk, https://feahasslarback.site123.me/blog/lenovo-mac-address-from-serial-number lenovo_mac_address_from_serial_number, https://bravlumoter.site123.me/blog/new-tamil-movie-download-in-tamilrockers new_tamil_movie_download_in_tamilrockers, https://crenperotic.site123.me/blog/minecraft-demosuz-indir-1122 minecraft_demosuz_indir_1.12.2, https://sighrihensti.site123.me/blog/kaspersky-total-security-2017-key kaspersky_total_security_2017_key, https://onswelarac.site123.me/blog/mount-and-blade-serial-key-youtube mount_and_blade_serial_key_youtube, https://diefridisla.site123.me/blog/kgf-full-movie-torrent-download-in-hindi kgf_full_movie_torrent_download_in_hindi, https://ungogorbirth.site123.me/blog/nox-app-player-android-44-2-emulator-for-pc nox_app_player_android_4.4_2_emulator_for_pc, https://bidamrehips.site123.me/blog/minecraft-full-version-pc-2019 minecraft_full_version_pc_2019, https://tempboshali.site123.me/blog/kendall-and-kylie-hack-2019 kendall_and_kylie_hack_2019, https://camrehouda.site123.me/blog/iso-9001-iso-27001-integration iso_9001_&_iso_27001_integration, https://mumtelanha.site123.me/blog/mcpe-block-launcher-apk mcpe_block_launcher_apk, https://tiobrigexnjum.site123.me/blog/konica-minolta-drivers-mac-el-capitan konica_minolta_drivers_mac_el_capitan, https://rhapcomulja.site123.me/blog/iso-final-fantasy-xii-international-zodiac-job-system iso_final_fantasy_xii_international_zodiac_job_system, https://crenperotic.site123.me/blog/logitech-k400-driver-software logitech_k400_driver_software, https://efapprosim.site123.me/blog/nwn-2-patch-download nwn_2_patch_download, https://speedearviena.site123.me/blog/ml1710-drivers ml1710_drivers, https://taupregteicomp.site123.me/blog/matlab-2013-free-download-with-crack-64-bit matlab_2013_free_download_with_crack_64_bit, https://taupregteicomp.site123.me/blog/music-making-games-unblocked music_making_games_unblocked, https://neumisstravin.site123.me/blog/mobo-market-apk-download mobo_market_apk_download, https://neumisstravin.site123.me/blog/microsoft-office-2007-torrent-crack microsoft_office_2007_torrent_crack, https://erpfafonti.site123.me/blog/norma-iso-10013-pdf-espaB1ol norma_iso_10013_pdf_espa単ol, https://hardcredenprop.site123.me/blog/minecraft-pe-sao-map-download minecraft_pe_sao_map_download, https://arpenvasel.site123.me/blog/iso-file-to-dvd-windows-10 iso_file_to_dvd_windows_10, https://cerncecygag.site123.me/blog/kim-hackney-goldcorp kim_hackney_goldcorp, https://cerncecygag.site123.me/blog/moto-racer-4-free-download moto_racer_4_free_download, https://bidamrehips.site123.me/blog/megadrive-emulator-android-apk megadrive_emulator_android_apk, https://parkbhagearno.site123.me/blog/mirror-apk-mod mirror_apk_mod, https://guetepkela.site123.me/blog/mac-linksys-router-setup mac_linksys_router_setup, https://diefridisla.site123.me/blog/ms-product-key-2019 ms_product_key_2019, https://peloceren.site123.me/blog/norton-internet-security-2012-product-key-free norton_internet_security_2012_product_key_free, https://peloceren.site123.me/blog/marshall-county-drivers-license marshall_county_drivers_license, https://binabwealthten.site123.me/blog/movie-app-hd-pro-apk movie_app_hd_pro_apk,
2019-06-21 14:56:20 Zudnpwvf
, https://swerisojcii.site123.me/blog/win-7-generic-bluetooth-driver win_7_generic_bluetooth_driver, https://lingcongeolo.site123.me/blog/9AB0BA-81BAB087B0828C-84B8BB8CBC-BDB0-B0B9BFB0B4 kak_skachat_film_na_aipad, https://hearttiserim.site123.me/blog/pro-music-mixer-free-download pro_music_mixer_free_download, https://quischickitperb.site123.me/blog/filemaker-pro-11-enter-license-key filemaker_pro_11_enter_license_key, https://tardomeaga.site123.me/blog/windows-7-bootable-dvd-iso-download-free windows_7_bootable_dvd_iso_download_free, https://quidearcigoo.site123.me/blog/nox-android-emulator-download-for-pc nox_android_emulator_download_for_pc, https://mozinrephu.site123.me/blog/lg-flash-tool-2014-64-bit-download lg_flash_tool_2014_64_bit_download, https://bumulpofi.site123.me/blog/download-driver-booster-55-free download_driver_booster_5.5_free, https://bankbralmepel.site123.me/blog/gta-vice-city-download-pc-full-version-free gta_vice_city_download_pc_full_version_free, https://brochinvila.site123.me/blog/download-minitool-partition-wizard-1023 download_minitool_partition_wizard_10.2.3, https://swerisojcii.site123.me/blog/tips-for-lyft-drivers-in-new-jersey tips_for_lyft_drivers_in_new_jersey, https://ditbarclyhou.site123.me/blog/wondershare-dr-fone-register-key wondershare_dr_fone_register_key, https://obpegedo.site123.me/blog/konica-minolta-bizhub-c3350-service-manual konica_minolta_bizhub_c3350_service_manual, https://neuverkema.site123.me/blog/windows-7-81BAB087B0828C-BE80B8B3B8BDB0BB8CBD8BB9-BEB180B0B7 windows_7_skachat_originalnyi_obraz, https://acdutona.site123.me/blog/gta-san-andreas-snow-download-torrent-pc gta_san_andreas_snow_download_torrent_pc, https://bankbralmepel.site123.me/blog/crack-za-gta-san-andreas-download crack_za_gta_san_andreas_download, https://sahpnerepos.site123.me/versions/2/wizard/modules/blog/addItem.php serial_number_avast_antivirus_2018, https://lingcongeolo.site123.me/blog/play-sim-girl-online-full-version play_sim_girl_online_full_version, https://quidearcigoo.site123.me/blog/texas-drivers-license-reinstatement-phone-number texas_drivers_license_reinstatement_phone_number, https://esygvolgesch.site123.me/blog/high-standard-supermatic-citation-serial-numbers high_standard_supermatic_citation_serial_numbers, https://ditbarclyhou.site123.me/blog/gtx-690-vs-gtx-1060 gtx_690_vs_gtx_1060, https://cubompawur.site123.me/blog/dllkit-pro-license-key-free-download dllkit_pro_license_key_free_download, https://batlapatwa.site123.me/blog/download-xenia-emulator-32-bit download_xenia_emulator_32_bit, https://ramudapppo.site123.me/blog/sony-serial-number-on-box sony_serial_number_on_box, https://pitcarbblande.site123.me/blog/galaxy-weather-on-lock-screen galaxy_weather_on_lock_screen, https://ovmorvoimeh.site123.me/blog/best-free-funny-movies-on-youtube best_free_funny_movies_on_youtube, https://restdiroben.site123.me/versions/2/wizard/modules/blog/addItem.php kinemaster_pro_apk_download_android, https://lingcongeolo.site123.me/blog/free-download-tuneup-utilities-2012-full-version-with-product-key free_download_tuneup_utilities_2012_full_version_with_product_key, https://obpegedo.site123.me/blog/utorrent-free-download-for-windows-7-64-bit utorrent_free_download_for_windows_7_64_bit, https://tenvidosuan.site123.me/blog/florida-drivers-license-test-points florida_drivers_license_test_points, https://pachbikdrgerin.site123.me/blog/windows-81-pro-serial-key-64-bit-free windows_8.1_pro_serial_key_64_bit_free, https://cejugeeta.site123.me/blog/dell-laptop-product-key-windows-7 dell_laptop_product_key_windows_7, https://pitcarbblande.site123.me/blog/gta-v-online-change-character-name gta_v_online_change_character_name, https://conworlsimpvas.site123.me/versions/2/wizard/modules/blog/addItem.php baazaar_2018_full_movie_watch_online_free_123movies, https://bumulpofi.site123.me/blog/download-borland-c-builder-6-full-version download_borland_c++_builder_6_full_version, https://quidearcigoo.site123.me/blog/most-popular-us-websites-2018 most_popular_us_websites_2018, https://tracinleton.site123.me/blog/movavi-video-suite-15-activation-key-crack movavi_video_suite_15_activation_key_crack, https://neuverkema.site123.me/blog/cardworks-business-card-software-plus-crack cardworks_business_card_software_plus_crack, https://ramisivi.site123.me/blog/can-you-play-downloaded-3ds-games-on-switch can_you_play_downloaded_3ds_games_on_switch, https://neuverkema.site123.me/blog/what-is-apk-and-obb-file what_is_apk_and_obb_file,
2019-06-21 16:20:03 Mnidqpct
, https://gresartertio.kinja.com/adobe-cs6-key-generator-download-1835707672 adobe_cs6_key_generator_download, https://nodenbattgar.kinja.com/download-game-nova-legacy-mod-hack-apk-1835698100 download_game_nova_legacy_mod_hack_apk, https://reipsychiltriph.kinja.com/download-facebook-messenger-for-windows-7-64-bit-free-1835697282 download_facebook_messenger_for_windows_7_64_bit_free, https://diavodihealth.kinja.com/descargar-google-play-store-para-ios-1835690591 descargar_google_play_store_para_ios, https://evcarbili.kinja.com/activation-synthesis-hypothesis-summary-1835700842 activation-synthesis_hypothesis_summary, https://tandbeachwbipguy.kinja.com/crackle-activate-mexico-1835714229 crackle_activate_mexico, https://tiawildoca.kinja.com/activation-troubleshooter-for-office-2010-1835692211 activation_troubleshooter_for_office_2010, https://lcosadchriste.kinja.com/apple-activation-server-down-apple-tv-1835692130 apple_activation_server_down_apple_tv, https://puupanclabve.kinja.com/descargar-driver-easy-pro-full-espanol-2019-1835715795 descargar_driver_easy_pro_full_espa単ol_2019, https://backsolpacyc.kinja.com/descargar-sony-vegas-pro-10-portable-espanol-gratis-1835696206 descargar_sony_vegas_pro_10_portable_espa単ol_gratis, https://reipsychiltriph.kinja.com/apex-legends-mobile-beta-apk-download-1835696720 apex_legends_mobile_beta_apk_download, https://traticeven.kinja.com/descargar-google-earth-gratis-para-pc-1835702155 descargar_google_earth_gratis_para_pc, https://lcosadchriste.kinja.com/android-custom-ringtone-for-text-messages-1835692616 android_custom_ringtone_for_text_messages, https://reridepolc.kinja.com/descargar-videos-de-youtube-sin-programas-2018-1835697569 descargar_v鱈deos_de_youtube_sin_programas_2018, https://weiderthari.kinja.com/descargar-arduino-ide-para-windows-1835717709 descargar_arduino_ide_para_windows, https://grandongahur.kinja.com/descargar-juegos-para-pc-pocos-requisitos-espanol-1835707942 descargar_juegos_para_pc_pocos_requisitos_espa単ol, https://tiawildoca.kinja.com/cannot-change-ringtone-ringtone-id-in-use-1835693530 cannot_change_ringtone_ringtone_id_in_use, https://piejubinca.kinja.com/download-games-nintendo-wii-iso-1835715886 download_games_nintendo_wii_iso, https://bertirinhu.kinja.com/crack-office-2016-windows-10-fr-1835706784 crack_office_2016_windows_10_fr, https://soticsettlows.kinja.com/download-excel-2016-free-for-pc-1835717418 download_excel_2016_free_for_pc, https://suimacomke.kinja.com/descargar-pdf-reader-pro-gratis-1835708485 descargar_pdf_reader_pro_gratis, https://lcosadchriste.kinja.com/apple-iphone-sms-ringtone-mp3-download-1835693292 apple_iphone_sms_ringtone_mp3_download, https://inthfulasex.kinja.com/best-tik-tok-video-status-download-1835709179 best_tik_tok_video_status_download, https://grandongahur.kinja.com/descargar-revista-muy-interesante-asesinos-en-serie-1835708213 descargar_revista_muy_interesante_asesinos_en_serie, https://taifortbreedan.kinja.com/crack-deflection-analysis-1835714565 crack_deflection_analysis, https://krimininex.kinja.com/a-long-crack-in-earths-crust-from-which-lava-may-flow-i-1835717546 a_long_crack_in_earths_crust_from_which_lava_may_flow_is_called_a, https://rioriegocom.kinja.com/basement-crack-repair-methods-1835703610 basement_crack_repair_methods, https://laubmibalde.kinja.com/descargar-whatsapp-uptodown-versiones-anteriores-1835716918 descargar_whatsapp_uptodown_versiones_anteriores, https://tiawildoca.kinja.com/crack-your-back-meaning-1835692451 crack_your_back_meaning, https://evcarbili.kinja.com/crack-serial-y-keygen-autocad-2014-1835699917 crack_serial_y_keygen_autocad_2014, https://rerarloka.kinja.com/download-google-sketchup-2019-free-1835707192 download_google_sketchup_2019_free, https://suimacomke.kinja.com/cant-download-app-on-samsung-smart-tv-1835709482 cant_download_app_on_samsung_smart_tv, https://clinconsfove.kinja.com/descargar-outlook-2013-full-mega-1835718607 descargar_outlook_2013_full_mega, https://sypmcephyhead.kinja.com/descargar-videos-youtube-mp3-iphone-1835715761 descargar_videos_youtube_mp3_iphone, https://clinconsfove.kinja.com/crackdown-3-update-april-1835718427 crackdown_3_update_april, https://molosoti.kinja.com/descargar-microsoft-office-2017-gratis-para-windows-10-1835712190 descargar_microsoft_office_2017_gratis_para_windows_10_mas_activador, https://rioriegocom.kinja.com/descargar-office-365-gratis-para-windows-8-1835704640 descargar_office_365_gratis_para_windows_8, https://lalencamam.kinja.com/descargar-snaptube-para-pc-windows-10-uptodown-1835715412 descargar_snaptube_para_pc_windows_10_uptodown, https://lcosadchriste.kinja.com/descargar-chrome-os-para-pc-espanol-1835691432 descargar_chrome_os_para_pc_espa単ol, https://rerarloka.kinja.com/descargar-netflix-en-mac-1835706367 descargar_netflix_en_mac, https://nevulpiaprov.kinja.com/download-adobe-reader-11-0-19-offline-installer-1835713517 download_adobe_reader_11.0.19_offline_installer, https://mitipoma.kinja.com/descargar-gratis-bluestacks-1-para-pc-1835700981 descargar_gratis_bluestacks_1_para_pc, https://inthfulasex.kinja.com/2006-honda-civic-cracked-engine-block-warranty-1835708734 2006_honda_civic_cracked_engine_block_warranty, https://mitipoma.kinja.com/arch-linux-i386-install-1835700317 arch_linux_i386_install, https://lcosadchriste.kinja.com/autodesk-activation-file-zip-1835691830 autodesk_activation_file.zip,
2019-06-21 19:39:26 Wdnmceaf
, https://www.uchi.kz/zapis-v-bloge/vanders-human-physiology-15th-edition vanders_human_physiology_15th_edition, https://www.uchi.kz/zapis-v-bloge/gamemaker-studio-master-collection-kickass gamemaker_studio_master_collection_kickass, https://www.uchi.kz/zapis-v-bloge/ms-office-professional-plus-2010-system-requirements ms_office_professional_plus_2010_system_requirements, https://www.uchi.kz/zapis-v-bloge/survivalcraft-multiplayer-apk-free-download-android survivalcraft_multiplayer_apk_free_download_for_android, https://www.uchi.kz/zapis-v-bloge/what-documents-are-needed-renew-drivers-license-michigan what_documents_are_needed_to_renew_drivers_license_in_michigan, http://archive.li/lMpJr underworld_blood_wars_sinhala_subtitles_free_download, http://archive.fo/fiAeT gta_v_upcoming_dlc_2018, https://www.uchi.kz/zapis-v-bloge/minecraft-pc-free-download-full-version-no-virus minecraft_pc_free_download_full_version_no_virus, https://www.uchi.kz/zapis-v-bloge/brother-p-touch-ql-500-drivers-windows-7 brother_p_touch_ql_500_drivers_windows_7, http://archive.vn/OlmTc arkadne_igre_za_pc_free_download, https://www.uchi.kz/zapis-v-bloge/find-my-ipad-version-serial-number#comment-42094 autocad_2014_full_version_free_download_utorrent, http://archive.li/2M4RT euro_truck_simulator_download_mobile, http://archive.is/V96dP security_key_card_activated_door, http://archive.li/urO4L discovering_statistics_using_spss_3rd_edition_andy_field_pdf, http://archive.is/UPsH8 3_idiots_english_sub_torrent_download, http://archive.li/vfFeY microsoft_office_2013_permanent_product_key, http://archive.vn/4wOeC top_movie_series_to_binge_watch, https://www.uchi.kz/zapis-v-bloge/adobe-after-effects-cs7-free-download-full-version adobe_after_effects_cs7_free_download_full_version, https://www.uchi.kz/zapis-v-bloge/department-safety-tn-drivers-license department_of_safety_tn_drivers_license, https://www.uchi.kz/zapis-v-bloge/eternity-warriors-2-mod-apk-revdl eternity_warriors_2_mod_apk_revdl, http://archive.is/eGwdW descargar_recover_my_files_gratis_crack_serial_y_keygen, https://www.uchi.kz/zapis-v-bloge/microsoft-office-2007-free-download-full-version-windows-10-64-bit-product-key microsoft_office_2007_free_download_full_version_for_windows_10_64_bit_with_product_key, http://archive.is/DqGjY league_of_stickman_mod_apk_latest_update, https://www.uchi.kz/zapis-v-bloge/meteor-garden-2-tagalog-version-full-movie-episodes-2018 meteor_garden_2_tagalog_version_full_movie_episodes_2018, http://archive.vn/e6jaG apk_mania_amazing_spiderman_2, https://www.uchi.kz/zapis-v-bloge/download-telugu-full-movies-free download_telugu_full_movies_free, http://archive.fo/ABoCq iobit_uninstaller_pro_key_7.1, https://www.uchi.kz/zapis-v-bloge/nba-2k19-legend-edition-price-philippines nba_2k19_legend_edition_price_philippines, https://www.uchi.kz/zapis-v-bloge/avira-antivirus-pro-2018-torrent-download avira_antivirus_pro_2018_torrent_download, http://archive.is/DEIRh hacking_software_free_download_for_windows_8.1, https://www.uchi.kz/zapis-v-bloge/realtek-bluetooth-driver-windows-10-free-download realtek_bluetooth_driver_windows_10_free_download, https://www.uchi.kz/zapis-v-bloge/xforce-keygen-inventor-2015-64-bit-free-download xforce_keygen_inventor_2015_64_bit_free_download, http://archive.vn/oYzjM system_mechanic_serial_key_2017, https://www.uchi.kz/zapis-v-bloge/editing-sentences-worksheet-2nd-grade editing_sentences_worksheet_2nd_grade, http://archive.is/FSh5J digital_license_instead_of_a_product_key, http://archive.vn/oa2XB download_lagu_keys_n_krates_-_dum_dee_dum_(jikay_remix)_official, https://www.uchi.kz/zapis-v-bloge/super-street-fighter-4-apk super_street_fighter_4_apk, http://archive.vn/I10Q5 what_is_ps2_free_mcboot, http://archive.li/jfJ8X pubg_free_download_for_iphone, https://www.uchi.kz/zapis-v-bloge/how-crack-torrent-zip-file-password how_to_crack_torrent_zip_file_password, https://www.uchi.kz/zapis-v-bloge/x360-controller-emulator-has-stopped-working x360_controller_emulator_has_stopped_working, http://archive.fo/cOfzW candy_crush_saga_soda_hack_tool, http://archive.li/SJiTV shadow_of_war_crack_torrent_download, https://www.uchi.kz/zapis-v-bloge/nvidia-gts-450-drivers-windows-7-32-bit nvidia_gts_450_drivers_windows_7_32_bit, http://archive.is/96KAj europa_universalis_4_1.28.3_patch_download, http://archive.vn/byQZT pex_ring_removal_tool_lowes, https://www.uchi.kz/zapis-v-bloge/pink-panther-2-download-free pink_panther_2_download_free, https://www.uchi.kz/zapis-v-bloge/texas-drivers-license-renewal-locations-dallas-tx texas_drivers_license_renewal_locations_dallas_tx, http://archive.is/nijpB microsoft_office_professional_plus_2013_key_generator,
What’s New in the k7 total security key 2016 Archives?
Screen Shot
System Requirements for K7 total security key 2016 Archives
- First, download the K7 total security key 2016 Archives
-
You can download its setup from given links:


