
Superantispyware for mac Archives

superantispyware for mac Archives
Question:Q:Recommendations for anti spyware
Looks like no one’s replied in a while. To start the conversation again, simply ask a new question.
Hello All,
I don't currently have any anti spyware software for my Mac and have been thinking that I need to get some. Someone advised me that I don't need an antivirus because there are no viruses made for Macs but that I should get some for trojans and spyware. He recommended Symantec paid for version and that I should just turn off the anti virus part to avoid my mac running slow.
Just wanted to see what the community thoughts were on this.
Thanks
MacBook Pro, Mac OS X (10.7.5)
Posted on
If you find this comment too long or too technical, read only sections 5, 6, and 10.
2. All versions of OS X since 10.6.7 have been able to detect known Mac malware in downloaded files, and to block insecure web plugins. This feature is transparent to the user, but internally Apple calls it "XProtect." The malware recognition database is automatically checked for updates once a day; however, you shouldn't rely on it, because the attackers are always at least a day ahead of the defenders.
The following caveats apply to XProtect:
- It can be bypassed by some third-party networking software, such as BitTorrent clients and Java applets.
- It only applies to software downloaded from the network. Software installed from a CD or other media is not checked.
Gatekeeper doesn't depend on a database of known malware. It has, however, the same limitations as XProtect, and in addition the following:
- It can easily be disabled or overridden by the user.
- A malware attacker could get control of a code-signing certificate under false pretenses, or could simply ignore the consequences of distributing codesigned malware.
- An App Store developer could find a way to bypass Apple's oversight, or the oversight could fail due to human error.
For the reasons given above, App Store products, and other applications recognized by Gatekeeper as signed, are safer than others, but they can't be considered absolutely safe. "Sandboxed" applications may prompt for access to private data, such as your contacts, or for access to the network. Think before granting that access. Sandboxing security is based on user input. Never click through any request for authorization without thinking.
4. Starting with OS X 10.8.3, a third layer of protection has been added: a "Malware Removal Tool" (MRT). MRT runs automatically in the background when you update the OS. It checks for, and removes, malware that may have evaded the other protections via a Java exploit (see below.) MRT also runs when you install or update the Apple-supplied Java runtime (but not the Oracle runtime.) Like XProtect, MRT is effective against known threats, but not against unknown ones. It notifies you if it finds malware, but otherwise there's no user interface to MRT.
Software from an untrustworthy source
- Software of any kind is distributed via BitTorrent or Usenet.
- Software with a corporate brand, such as Adobe Flash Player, doesn't come directly from the developer’s website.
- Rogue websites such as Softonic and CNET Download distribute free applications that have been packaged in a superfluous "installer."
- The software is advertised by means of spam or intrusive web popups.
Software that is plainly illegal or does something illegal
- Software that you would otherwise have to pay for is "cracked" or "free."
- An application helps you to infringe copyright, for instance by circumventing the copy protection on commercial software, or saving streamed media for reuse without permission.
Conditional or unsolicited offers from strangers
- A web page tells you that you have a “virus” and offers to help you remove it. (Some reputable websites did legitimately warn visitors who were infected with the "DNSChanger" malware. That exception to this rule no longer applies.)
- A web site offers free content such as video or music, but to use it you must install a “codec,” “plug-in,” "player," "downloader," "extractor," or “certificate” that comes from that same site, or an unknown one.
- You win a prize in a contest you never entered.
- Someone on a message board such as this one is eager to help you, but only if you install an application of his choosing.
- A "FREE WI-FI !!!" network advertises itself in a public place such as an airport, but is not provided by the management.
- You open what looks like a document and get an alert that it's "an application downloaded from the Internet." Click Cancel and delete the file or message.
- An application does something inexplicable, such as asking for permission to access your contacts, your location, or the Internet for no obvious reason.
- Software is attached to email that you didn't request, even if it comes (or seems to come) from someone you trust.
I don't say that leaving the safe harbor just once will necessarily result in disaster, but making a habit of it will weaken your defenses against malware attack. Any of the above scenarios should, at the very least, make you uncomfortable.
6. Java on the Web ( not to be confused with JavaScript, to which it's not related, despite the similarity of the names) is a weak point in the security of any system. Java is, among other things, a platform for running complex applications in a web page, on the client. That was always a bad idea, and Java's developers have proven themselves incapable of implementing it without also creating a portal for malware to enter. Past Java exploits are the closest thing there has ever been to a Windows-style virus affecting OS X. Merely loading a page with malicious Java content could be harmful.Fortunately, client-side Java on the Web is obsolete and mostly extinct. Only a few outmoded sites still use it. Try to hasten the process of extinction by avoiding those sites, if you have a choice. Forget about playing games or other non-essential uses of Java.
7. Never install any commercial "anti-virus" or "Internet security" products for the Mac, as they all do more harm than good, if they do any good at all. If you need to be able to detect Windows malware in your files, use one of the free security apps in the Mac App Store — nothing else.
- To recognize malware, the software depends on a database of known threats, which is always at least a day out of date. New threats are emerging on a daily basis. Research has shown that most successful attacks are "zero-day" — that is, previously unknown. Recognition-based malware scanners do not defend against such attacks.
- Their design is predicated on the nonexistent threat that malware may be injected at any time, anywhere in the file system. Malware is downloaded from the network; it doesn't materialize from nowhere.
- In order to meet that nonexistent threat, the software modifies or duplicates low-level functions of the operating system, which is a waste of resources and a common cause of instability, bugs, and poor performance.
- By modifying the operating system, the software itself may create weaknesses that could be exploited by malware attackers.
8. An anti-malware product from the App Store, such as "ClamXav," has the same drawback as the commercial suites of being always out of date, but it does not inject code into the operating system. That doesn't mean it's entirely harmless. It may report email messages that have "phishing" links in the body, or Windows malware in attachments, as infected files, and offer to delete or move them. Doing so will corrupt the Mail database. The messages should be deleted from within the Mail application.
A Windows malware attachment in email is usually easy to recognize. The file name will often be targeted at people who aren't very bright; for example:
♥♥♥♥♥♥♥♥♥♥♥♥♥♥!!!!!!!H0TBABEZ4U!!!!!!!.AVI♥♥♥♥♥♥♥♥♥♥♥♥♥♥.exe
The ClamXav developer won't try to "upsell" you to a paid version of the product. Other developers may do that. Don't be upsold. For one thing, you should not pay to protect Windows users from the consequences of their choice of computing platform. For another, a paid upgrade from a free app will probably have all the disadvantages mentioned in section 7.
Posted on
Feb 2, 2014 6:05 AM in response to Trigger1882 In response to Trigger1882
Oh Dear
many person here will say not needed others will say
Sophos free for home use or Clam XAV from the apple store (free)
I personally use sophos also free
http://www.sophos.com/en-us/products/free-tools/sophos-antivirus-for-mac-home-ed ition.aspx
good luck see more like this to the right of the page...........
Feb 2, 2014 3:05 PM in response to Trigger1882 In response to Trigger1882
Trigger1882 wrote:
I don't currently have any anti spyware software for my Mac
And as long as you don't allow physical access to your computer or your network, you won't need any, as there currently is no other known way to install such software.
The only anti-spyware software available for the Mac is MacScan from SecureMac. It is prone to false alarms, so make certain that anything it finds is actually what it says it is. It is also almost totally ineffective at finding other types of malware.
Page content loaded
Feb 2, 2014 6:05 AM in response to Trigger1882 In response to Trigger1882
Oh Dear
many person here will say not needed others will say
Sophos free for home use or Clam XAV from the apple store (free)
I personally use sophos also free
http://www.sophos.com/en-us/products/free-tools/sophos-antivirus-for-mac-home-ed ition.aspx
good luck see more like this to the right of the page...........
Feb 2, 2014 6:05 AM
Feb 2, 2014 6:22 AM in response to Trigger1882 In response to Trigger1882
Hi Trigger1882,
I also have no spyware software on my Macbook Pro. I enabled gatekeeper ( http://support.apple.com/kb/HT5290 , and it´s available since Mac OS X 10.7.5) and I think that's good enough, but it's better if you protect your Mac additionally by such software. A Mac is a work machine, I think that your Mac is not particularly slow.
Sorry for my bad englisch, I´am a young german student. 😉
Greetings from Germany
macprofi123
Feb 2, 2014 6:22 AM
Feb 2, 2014 8:59 AM in response to Trigger1882 In response to Trigger1882
If you find this comment too long or too technical, read only sections 5, 6, and 10.
2. All versions of OS X since 10.6.7 have been able to detect known Mac malware in downloaded files, and to block insecure web plugins. This feature is transparent to the user, but internally Apple calls it "XProtect." The malware recognition database is automatically checked for updates once a day; however, you shouldn't rely on it, because the attackers are always at least a day ahead of the defenders.
The following caveats apply to XProtect:
- It can be bypassed by some third-party networking software, such as BitTorrent clients and Java applets.
- It only applies to software downloaded from the network. Software installed from a CD or other media is not checked.
Gatekeeper doesn't depend on a database of known malware. It has, however, the same limitations as XProtect, and in addition the following:
- It can easily be disabled or overridden by the user.
- A malware attacker could get control of a code-signing certificate under false pretenses, or could simply ignore the consequences of distributing codesigned malware.
- An App Store developer could find a way to bypass Apple's oversight, or the oversight could fail due to human error.
For the reasons given above, App Store products, and other applications recognized by Gatekeeper as signed, are safer than others, but they can't be considered absolutely safe. "Sandboxed" applications may prompt for access to private data, such as your contacts, or for access to the network. Think before granting that access. Sandboxing security is based on user input. Never click through any request for authorization without thinking.
4. Starting with OS X 10.8.3, a third layer of protection has been added: a "Malware Removal Tool" (MRT). MRT runs automatically in the background when you update the OS. It checks for, and removes, malware that may have evaded the other protections via a Java exploit (see below.) MRT also runs when you install or update the Apple-supplied Java runtime (but not the Oracle runtime.) Like XProtect, MRT is effective against known threats, but not against unknown ones. It notifies you if it finds malware, but otherwise there's no user interface to MRT.
Software from an untrustworthy source
- Software of any kind is distributed via BitTorrent or Usenet.
- Software with a corporate brand, such as Adobe Flash Player, doesn't come directly from the developer’s website.
- Rogue websites such as Softonic and CNET Download distribute free applications that have been packaged in a superfluous "installer."
- The software is advertised by means of spam or intrusive web popups.
Software that is plainly illegal or does something illegal
- Software that you would otherwise have to pay for is "cracked" or "free."
- An application helps you to infringe copyright, for instance by circumventing the copy protection on commercial software, or saving streamed media for reuse without permission.
Conditional or unsolicited offers from strangers
- A web page tells you that you have a “virus” and offers to help you remove it. (Some reputable websites did legitimately warn visitors who were infected with the "DNSChanger" malware. That exception to this rule no longer applies.)
- A web site offers free content such as video or music, but to use it you must install a “codec,” “plug-in,” "player," "downloader," "extractor," or “certificate” that comes from that same site, or an unknown one.
- You win a prize in a contest you never entered.
- Someone on a message board such as this one is eager to help you, but only if you install an application of his choosing.
- A "FREE WI-FI !!!" network advertises itself in a public place such as an airport, but is not provided by the management.
- You open what looks like a document and get an alert that it's "an application downloaded from the Internet." Click Cancel and delete the file or message.
- An application does something inexplicable, such as asking for permission to access your contacts, your location, or the Internet for no obvious reason.
- Software is attached to email that you didn't request, even if it comes (or seems to come) from someone you trust.
I don't say that leaving the safe harbor just once will necessarily result in disaster, but making a habit of it will weaken your defenses against malware attack. Any of the above scenarios should, at the very least, make you uncomfortable.
6. Java on the Web ( not to be confused with JavaScript, to which it's not related, despite the similarity of the names) is a weak point in the security of any system. Java is, among other things, a platform for running complex applications in a web page, on the client. That was always a bad idea, and Java's developers have proven themselves incapable of implementing it without also creating a portal for malware to enter. Past Java exploits are the closest thing there has ever been to a Windows-style virus affecting OS X. Merely loading a page with malicious Java content could be harmful.Fortunately, client-side Java on the Web is obsolete and mostly extinct. Only a few outmoded sites still use it. Try to hasten the process of extinction by avoiding those sites, if you have a choice. Forget about playing games or other non-essential uses of Java.
7. Never install any commercial "anti-virus" or "Internet security" products for the Mac, as they all do more harm than good, if they do any good at all. If you need to be able to detect Windows malware in your files, use one of the free security apps in the Mac App Store — nothing else.
- To recognize malware, the software depends on a database of known threats, which is always at least a day out of date. New threats are emerging on a daily basis. Research has shown that most successful attacks are "zero-day" — that is, previously unknown. Recognition-based malware scanners do not defend against such attacks.
- Their design is predicated on the nonexistent threat that malware may be injected at any time, anywhere in the file system. Malware is downloaded from the network; it doesn't materialize from nowhere.
- In order to meet that nonexistent threat, the software modifies or duplicates low-level functions of the operating system, which is a waste of resources and a common cause of instability, bugs, and poor performance.
- By modifying the operating system, the software itself may create weaknesses that could be exploited by malware attackers.
8. An anti-malware product from the App Store, such as "ClamXav," has the same drawback as the commercial suites of being always out of date, but it does not inject code into the operating system. That doesn't mean it's entirely harmless. It may report email messages that have "phishing" links in the body, or Windows malware in attachments, as infected files, and offer to delete or move them. Doing so will corrupt the Mail database. The messages should be deleted from within the Mail application.
A Windows malware attachment in email is usually easy to recognize. The file name will often be targeted at people who aren't very bright; for example:
♥♥♥♥♥♥♥♥♥♥♥♥♥♥!!!!!!!H0TBABEZ4U!!!!!!!.AVI♥♥♥♥♥♥♥♥♥♥♥♥♥♥.exe
The ClamXav developer won't try to "upsell" you to a paid version of the product. Other developers may do that. Don't be upsold. For one thing, you should not pay to protect Windows users from the consequences of their choice of computing platform. For another, a paid upgrade from a free app will probably have all the disadvantages mentioned in section 7.
Feb 2, 2014 8:59 AM
Feb 2, 2014 3:05 PM in response to Trigger1882 In response to Trigger1882
Trigger1882 wrote:
I don't currently have any anti spyware software for my Mac
And as long as you don't allow physical access to your computer or your network, you won't need any, as there currently is no other known way to install such software.
The only anti-spyware software available for the Mac is MacScan from SecureMac. It is prone to false alarms, so make certain that anything it finds is actually what it says it is. It is also almost totally ineffective at finding other types of malware.
Feb 2, 2014 3:05 PM
Question:Q:Recommendations for anti spyware
SuperAntiSpyware Review 2020

SuperAntiSpyware is an antivirus program that secures your PC from malware and hacker attacks. Its main purpose is to block spyware and other types of malicious software that infects a computer. Also, it provides users with the ability to perform advanced settings, use several scanning options, and work with various system tools when they try to restore some stability of Windows.
SuperAntiSpyware Pros and Cons
- Compatibility with all versions of Windows, starting with XP.
- It has several scanning modes and many useful system tools.
- The new System Investigator module provides comprehensive information about many parts of the system.
- It shows very good scanning results.
- The program generated a lot of false positives during the testing.
- There is no way to cancel the threat removal task.
- The System Investigator module does not provide the ability to manage applications and objects or create reports. Also, during our tests, it crashed when we tried to cancel it.
- There is no reference guide built into the application.
- When it comes to malware detection, SUPERAntiSpyware is pretty weak. It detected and deleted 4,195 virus samples from 8,502 files in total in our tests, so we can assume that her success rate was approximately 49%.
Highlights
- Detection and removal of spyware and other malicious software
- Multiple scan modes: full, fast, critical, selective
- Highly detalized scan reports
- Advanced scanner settings
- System Detailed Analysis Module (System Investigator)
- Uninstallation of unwanted programs
- Removal of hard-to-delete files
- Quarantine mode
- Fixing of the registry corruption caused by malware
Main Features
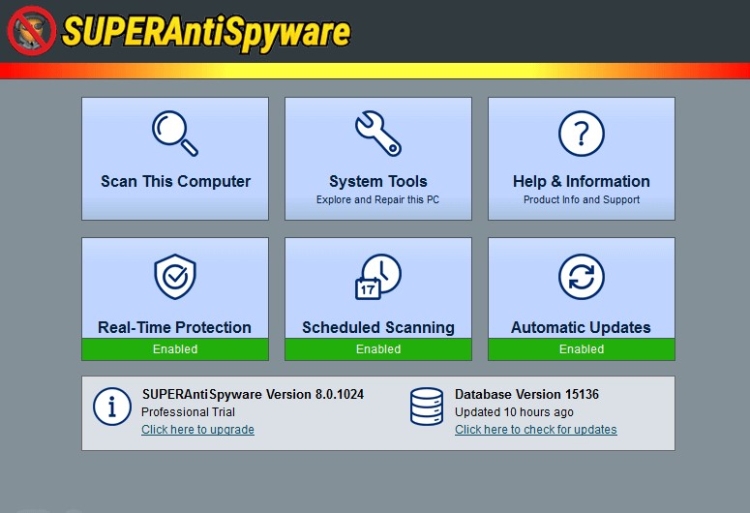
The company makes the biggest emphasis on the elimination of identity threats and the security of one’s personal data. SuperAntiSpyware is an advanced security program designed to ensure the confidentiality of the information and prevent intrusions by blocking all popular spyware types. It can also detect other forms of malicious software, such as free adware, Trojans, worms, and rootkits, but this should only be taken as additional security measures since the application was not created as a full-fledged antivirus. Here is the list of the features introduced by the developers:
- Malware
- Spyware
- Adware
- Trojans
- Worms
- Ransomware
- Keyloggers
- Hijackers
- Rootkits
- PUPs
- Cryptominers
The free version of SuperAntiSpyware Free has a redesigned interface that simplifies navigation for inexperienced users, supports touch control on tablets running Windows. This new tool explores various parts of the system, as well as improvements in scanning speed, system resources, the Help menu, and overall application stability.
More features are available in SuperAntiSpyware Professional, such as scheduled scans, a new email notification system to receive the results of scheduled checks, real-time blocking of spyware, and automatic checks for program updates and antivirus databases.
Security Features
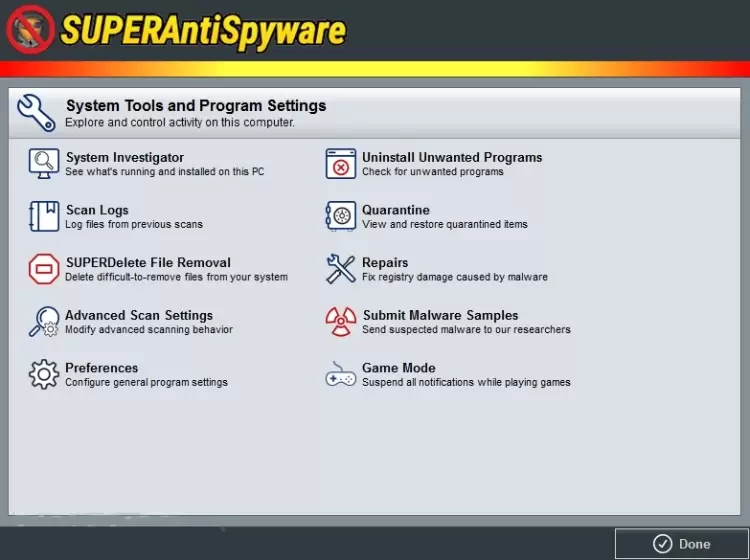
The program contains several security features that make the use of the computer and your identity safe. The main three of the security features are as follows.
- Real-Time Threat Blocking. It is the feature that receives constant updates about emerging viruses and new threats. With it, the antivirus can block even zero-day threats or remove them from your computer before they do any damage. You can customize the threat detection or scan the computer when you need it.
- Detect & Remove Malicious Threats. The program protects from the major virtual threats, such as Trojans, ransomware, spyware, and other types of malware. It has an option of automatic removal of threats or the manual one, which requires the user’s participation. It is important to mention that the program demonstrated a lot of false-positive alarms, which is why it is better to confirm threat removal manually.
- Email Notifications. You can set the program to notify you about all the security activities via email. If anything is wrong with your computer while you are away, you will get the note in your inbox. However, if there are too many notifications, you can always cancel the email subscription.
Scanning Options
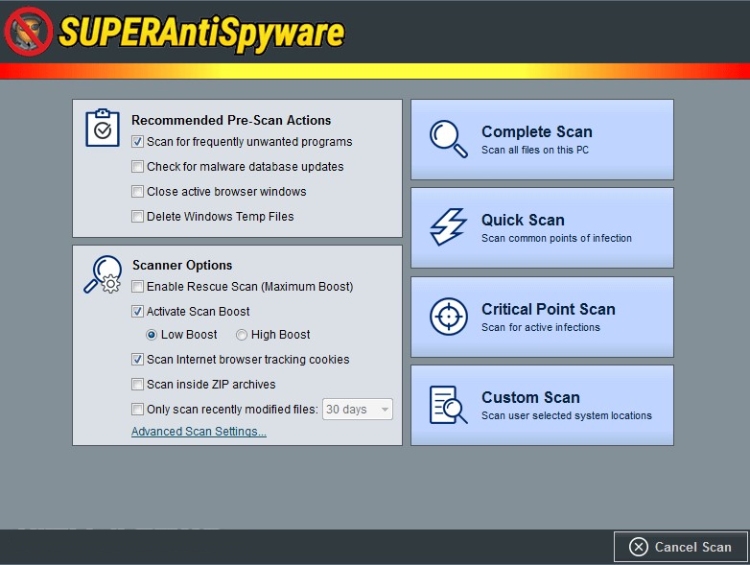
There are four scanning options:
- the Complete mode performs a full scan on all parts of the computer;
- in the Quick mode, only the most characteristic places of hiding spyware are viewed so as not to lose speed;
- in the Critical Point mode (scan of critical objects), only active infections,
- while using the Custom mode, you can select specific objects for scanning.
SuperAntiSpyware shows you a list of several recommended actions to take before scanning. It can check the gear for unwanted programs, scan it for malware database updates, close windows of active browsers, and delete temporary Windows files. As for the scanning itself, you can enable the Rescue Scan (in case of severe malware infections) and Scan Boost, as additional system resources are allocated to speed up the scanning process). You can also set it to check web tracking browser cookies, scan the contents of ZIP archives, and check only recently modified files and set the number of days to be taken into account.
For advanced users, there are more scan settings. For example, it is possible to view only registered file types to reduce the task time, enable Alternate Data Streams, during scanning, check the operation of shortcuts, neutralize active threats before sending them to quarantine, and also ignore files larger than less than 4 MB, and non-executable files.
Performance
The antivirus shows little impact on the computer’s performance. However, the more complicated scan option you run, the more load it brings to the computer. If you are worried about the performance of the gear and do not want any software to slow it down, you need to set the antivirus the right way and always choose the scanning modes that are relevant for the particular situation.
As for the test results, SuperAntiSpyware shows quite a high sensitivity to most of the suspicious files. However, it also showed a lot of positive results for the files that did not contain any threats, which is why we would recommend revising the scanning results. The problem is, it can quarantine the clean files. Nonetheless, it did not miss the crucial threats to the security of the data and the machine. Hence, with the right custom settings and attention to the scan results, the software will not overload your computer or miss significant threats.
Ease of Use
The interface of the program is understandable and user-friendly. The developers guide you as a user from the very installation link on the website. All the major options and actions are easy to find, and access from the program’s home screen. Also, it is possible to mark any files that can be trusted, delete items marked by the application for deletion, and create a list of locations for automatic exclusion. All these actions are intuitive and laid out in the SuperAntiSpyware interface.
When you run a scan, the software utility displays the name, description, and registry key for each unwanted program that it finds. It gives users the ability to mark them as approved or uninstall them. If the computer has not been serviced for a long time, you can view the scan statistics later in the log, which will show details such as the type of scan, the total time, the total number of threats in each category, as well as the full path to each suspicious object. Overall, it is hard to get confused by the program or its functions.
Setup
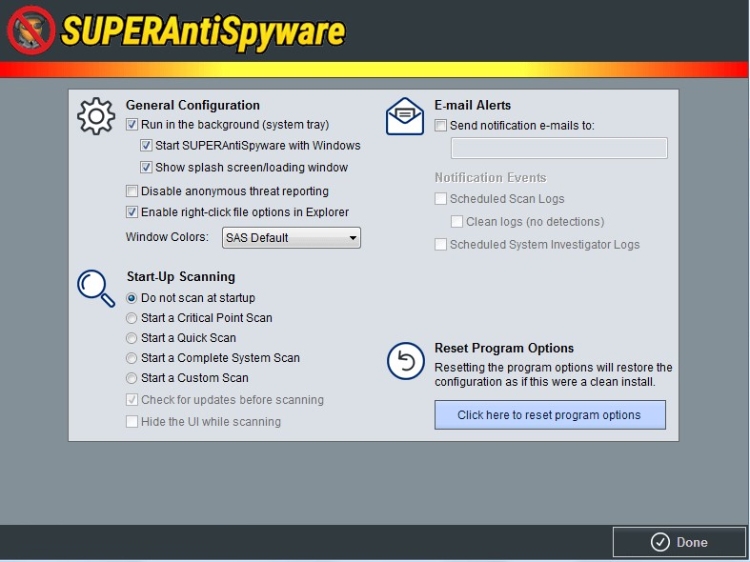
The installation process is quick and does not require any specific skills. During the installation process, you can choose an interface language and enable SuperAntiSpyware to check for fresh updates to the definition database and send system diagnostics to help identify potentially harmful software. Since there is an advertising component, the program will also offer to download and install third-party software tools that are not required for the program to work properly, but their installation can be excluded.
In the department responsible for the SuperAntiSpyware interface, they shrugged off the old execution structure. They chose the large flat buttons that were adopted by most software developers who decided to implement the look of the Metro interface. However, the theme and colors of the program remained mostly the same.
Using the buttons in the main window, you can immediately access the scanning functions, system tools, and reference documentation. The other three are only available in the SuperAntiSpyware Pro version with real-time protection, scheduled scans, automatic updates, so in the free version, they just annoy the user.
SuperAntiSpyware Pricing
There are two options you can take in the SuperAntiSpyware plans: the free one and the Pro one. Most of the crucial features are there is the free plan, yet, the paid suit has advanced features: real-time protection, scheduled scans, automatic updates, so in the free version, they just annoy the user. The features that are available in the free plan are Detection and Removal of Malicious Threats, Multi-Dimensional Scanning, and Process Interrogation Technology.
The advanced features in the Pro plan are Real-Time Threat Blocking, Automatic Updates, Multiple Scan Options, Email Notifications. The professional plan will cost you $29.95 per year and protect only one computer. You can try it for free, as there is a 14-day trial period for the Pro package.
Support and Customer Service

If you have questions or issues with the program, there are several options for you to get help. First, there is an extensive FAQ section on the website. It collects all the popular help requests and explains how to handle them. Second, there is a specified forum regarding the program and the complications that users encounter. You can learn from the experience of other users or ask your question in the community. Third, there is a semi-automated technical support department. It forks as follows: you choose the issue you have with the software and explain what is wrong. Finally, there is a contact form on the website. You can explain what your issue is in the form and wait until the support team contacts you via email. Here, whatever the problem is, you can find a way to solve it, as there are plenty of resources for that.
For billing issues, you can contact via phone: 866-966-6254, or utilize the following emails:
SuperAntiSpyware Alternatives
Of course, there are many different antiviruses in the market. If you are looking for an alternative or want to switch from SuperAntiSpyware. The most popular and reliable alternatives are:
SuperAntiSpyware Antivirus FAQ
Verdict
So, is SuperAntiSpyware a good choice to ensure the security of your computer? Well, it does great at protecting the computer from spyware. However, it cannot perform as a well-rounded, holistic antivirus. If you need a single antivirus with no additional security software, you may need to keep looking. However, if your concern is the security of your data, SuperAntiSpyware will provide you with it.
Is SUPERAntiSpyware a good program?
Is SUPERAntiSpyware a virus?
Which is better SUPERAntiSpyware or Malwarebytes?
Does SUPERAntiSpyware remove viruses?
Does SUPERAntiSpyware work with Windows 10?

SUPERAntiSpyware
SUPERAntiSpyware is the one of the most thorough scanners available on the market today. The Multi-Dimensional Scanning and Process Interrogation Technology is able to detect spyware, adware, trojans, ransomware, malware, and infections that other products miss!
SUPERAntiSpyware lets you repair broken Internet Connections, Desktops, Registry Editing and more with the unique Repair System. Dedicated Threat Research Team scours the web for new threats and provides daily definition updates.
SUPERAntiSpyware features highly advanced Real-Time Protection technology, to ensure protection from installation or re-installation of potential threats as you surf the Internet. Used in conjunction with First Chance Prevention and Registry Protection tools, your computer is protected from thousands of threats that attempt to infect and infiltrate your system at startup or while shutting down your system.
With SUPERAntiSpyware on your system you can detect and Remove Spyware, Adware, Malware, Trojans, Dialers, Worms, KeyLoggers, HiJackers, Parasites, Rootkits, Rogue Security Products and many other types of threats.
It is light on system resources and won't slow down your computer; unlike many other anti-spyware products, and it won't conflict with your existing anti-spyware or anti-virus solution! So, if you are looking for a solid, functional malware scanner, then you can't go far wrong with SUPERAntiSpyware.
What’s New in the superantispyware for mac Archives?
Screen Shot
System Requirements for Superantispyware for mac Archives
- First, download the Superantispyware for mac Archives
-
You can download its setup from given links:


